
Information Systems
Education Journal
Volume 21, No. 2
May 2023
ISSN: 1545-679X
In this issue:
We’re happy to have another great group of papers, along with a teaching case and a teaching exercise.
The general theme of the issue is the broad topic of student skills – skills that our employers want, skills
that our students are seeking, and skills that will serve as foundations for helping our students to become
great IS practitioners, as well as great future educators. This focusing on skills for both Computer
Science and Business courses, leveraging concepts from IS, assessing mobile learning and skill
development, and learning design and development, robotic process automation, and Internet of Things.
Never a dull moment in the IS community, and there’s more to come!
4. Enhancing Learning in Business Education Utilizing Project Management
Practice and Skills
Julia Fullick-Jagiela, Quinnipiac University
Patricia Kelly, Quinnipiac University
Amy KB Paros, Quinnipiac University
Iddrisu Awudu, Quinnipiac University
Susan Riello, Quinnipiac University
14. Enforcement of Prerequisites in Computer Science
Ernst Bekkering, Northeastern State University
Patrick Harrington, Northeastern State University
38. Mid-Pandemic Impact on Mobile Learning Motivation Factors
Neelima Bhatnagar, University of Pittsburgh
Ann-Marie Horcher, Northwood University
56. A Proposal for Combining Project Based Learning and Lean Six Sigma to
Teach Robotic Process Automation Development and Enhance Systems
Integration
William H. Money, The Citadel
Lionel Q. Mew, University of Richmond
69. Teaching Case:
Alexa, Help Me Learn About the Internet of Things!
Mark Frydenberg, Bentley University
82. Teaching Case:
A Registration System for a Citywide Service Project: Design & Development
Case
Dana Schwieger, Southeast Missouri State University
.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 2
https://isedj.org/; https://iscap.info
The Information Systems Education Journal (ISEDJ) is a double-blind peer-reviewed
academic journal published by ISCAP (Information Systems and Computing Academic
Professionals). Publishing frequency is five times per year. The first year of publication was
2003.
ISEDJ is published online (https://isedj.org). Our sister publication, the Proceedings of
EDSIGCON (https://proc.iscap.info) features all papers, abstracts, panels, workshops, and
presentations from the conference.
The journal acceptance review process involves a minimum of three double-blind peer
reviews, where both the reviewer is not aware of the identities of the authors and the authors
are not aware of the identities of the reviewers. The initial reviews happen before the ISCAP
conference. All papers, whether award-winners or not, are invited to resubmit for journal
consideration after applying feedback from the Conference presentation. Award winning papers
are assured of a publication slot; however, all re-submitted papers including award winners are
subjected to a second round of three blind peer reviews to improve quality and make final
accept/reject decisions. Those papers that are deemed of sufficient quality are accepted for
publication in the ISEDJ journal. Currently the target acceptance rate for the journal is under
36%.
Information Systems Education Journal is pleased to be listed in the Cabell's Directory of
Publishing Opportunities in Educational Technology and Library Science, in both the electronic
and printed editions. Questions should be addressed to the editor at [email protected] or the
publisher at publisher@isedj.org. Special thanks to members of ISCAP who perform the
editorial and review processes for ISEDJ.
2023 ISCAP Board of Directors
Jeff Cummings
Univ of NC Wilmington
President
Anthony Serapiglia
Saint Vincent College
Vice President
Eric Breimer
Siena College
Past President
Jennifer Breese
Penn State University
Director
Amy Connolly
James Madison University
Director
RJ Podeschi
Millikin University
Director/Treasurer
Michael Smith
Georgia Institute of Technology
Director/Secretary
David Woods
Miami University (Ohio)
Director
Jeffry Babb
West Texas A&M University
Director/Curricular Items Chair
Tom Janicki
Univ of NC Wilmington
Director/Meeting Facilitator
Paul Witman
California Lutheran University
Director/2023 Conf Chair
Xihui “Paul” Zhang
University of North Alabama
Director/JISE Editor
Copyright © 2023 by Information Systems and Computing Academic Professionals (ISCAP). Permission to make
digital or hard copies of all or part of this journal for personal or classroom use is granted without fee provided that
the copies are not made or distributed for profit or commercial use. All copies must bear this notice and full citation.
Permission from the Editor is required to post to servers, redistribute to lists, or utilize in a for-profit or commercial
use. Permission requests should be sent to Paul Witman, Editor, editor@isedj.org.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 3
https://isedj.org/; https://iscap.info
Information Systems
Education Journal
Editors
Paul Witman
Editor
California Lutheran
University
Thomas Janicki
Publisher
U of North Carolina
Wilmington
Dana Schwieger
Associate Editor
Southeast Missouri
State University
Ira Goldstein
Teaching Cases & Exercises
Co-Editor
Siena College
Michelle Louch
Teaching Cases & Exercises
Co-Editor
Duquesne University
Donald Colton
Emeritus Editor
Brigham Young University
Hawaii
Jeffry Babb
Emeritus Editor
West Texas A&M
University

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 4
https://isedj.org/; https://iscap.info
Enhancing Learning in Business Education
Utilizing Project Management Practice and Skills
Julia Fullick-Jagiela
Management Department
Patricia S. Kelly
Management Department
Amy KB Paros
Management Department
Iddrisu Awudu
Management Department
Susan Riello
Instructional Design Department
Quinnipiac University
Hamden, CT 06518 USA
Abstract
While industries compete to hire capable employees, it is essential that business education curriculum
delivers graduates who can solve complex problems and implement multifaceted solutions. This
approach to curriculum design focuses on developing project management skills to deliver an integrated,
student-centered methodology across multiple disciplines. The development of undergraduate
curriculum with a project management approach provides a framework centered on developing essential
career skills in critical thinking, decision-making, and problem-solving.
Keywords: business education, project management, curriculum development, student-centered
learning, project-based instruction
1. INTRODUCTION
As industry demands trained knowledge workers
who can synthesize data, think critically, and
develop solutions, undergraduate curriculum
must evolve (Rocca, 2010). A well-designed
undergraduate curriculum within a dynamic and
rapidly evolving industry supports student
recruitment, program reputation, and prepares
students for careers (Thai, De Wever, & Valcke,

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 5
https://isedj.org/; https://iscap.info
2017). Coupled with employer expectations,
current students demand higher levels of
engagement and practical classroom
experiences. Undergraduate curriculum founded
on active student-centered learning can meet this
need and deliver increased problem solving,
stronger critical thinking, and more developed
organizational skills (Rocca, 2010;
Vandenhouten, Groessl & Levintova, 2017).
Project management skills development can help
support embedding industry tested methodology
into curriculum. This can help to provide a set of
principles to explain process and structure into
course design assignments (Morrison, Ross, &
Kemp, 2005). Implementing skills development
and project management processes can help
faculty develop interactive, and well-designed
courses.
Curriculum development throughout
undergraduate education has not done enough to
leverage the innovation of project management
practice and skills development across
undergraduate curriculum. Our goal is to share an
approach utilized effectively in our own
curriculum redesign process. We believe that this
advancement in the curriculum will better serve
business students' needs and provide structure to
project work across the curriculum. In our
classroom, students can often struggle with basic
introductory project management processes.
While certain departments such as CIS and
Management offer foundational project
management-specific courses, we have surveyed
students in introductory courses and capstone
courses to determine the overall increase in their
project management skill and application. We
propose that integrating project management
practice should be included across the core
business curriculum. As evidenced by recent
survey collections, it is imperative that we provide
foundational project management skills
development, earlier in our curriculum starting
with first-year business core curriculum.
Foundational applications of project management
methodologies can be applied consistently
throughout student course work and team
projects. Information Systems and Management
programs can be instrumental in helping to
provide context and training by offering
fundamentals of project management class
options via general education requirements to
benefit students across disciplines. The time has
come to breakdown silos and expand curriculum
access so students across majors can gain these
critical skills that apply to all professions and
industries.
Project management allocates setting goals and
meeting due dates. Emerging time management
practices can increase student efficiency and
desired outcomes. In this ever-evolving
workplace, enhancing communication skills would
benefit students and employers. Communication
within a project team is essential to project
success. Iterative project management practices
such as Agile are helping project managers
provide benefits throughout the project's
lifecycle. This trend is becoming relevant for
students to understand and value as project
management practice evolves. If faculty do not
stay current with industry practices, we feel there
is a disservice to our students’ future applications.
Project management practice often encompasses
recognizing and addressing real-world problems.
Project management includes working with a
team of various subject matter experts to
complete a common goal. Students can advance
skills to understand several aspects of project
work such as managing deadlines, allocation of
specific resources, the value of time, and the
impact on budgets and cost.
Overall, improvement of project management
skills in undergraduate curriculum, across
multiple disciplines (not just computer
information systems or business) can support
students in both academic and professional
growth. They can also develop valuable and
marketable skills that will be useful in their future
careers (Karanja & Grant, 2020).
Additionally, recent project management trends
indicate we should continue to focus on education
related to developing interpersonal skills essential
to project management practice. Creating
curriculum that includes team-based leadership
exercises can help develop these skills.
Experiential learning project-based assignments
should be integrated consistently across the
entire undergraduate degree program to improve
curriculum and to more effectively train students
to adapt and thrive amidst common business
disruptions. Karanja and Grant (2020) also
stressed the importance of real-world project
management assessments.
2. LITERATURE REVIEW
As research has identified, pedagogy must align
with employer expectations of graduate skills
(Daniel, 2012). There is a growing demand for
project management courses that prepare
graduates with skills in professional
communication, critical thinking, collaborative
problem-solving, and critical reflection (Gharaie &

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 6
https://isedj.org/; https://iscap.info
Wingrove, 2020). Business classrooms allow
students to engage in an applied approach to
active learning both online and in-person (Martin
& Bolliger, 2018) which can further increase
knowledge through application, engagement, and
problem-based learning. Students must explore
challenges using data to find the root cause
analysis, generate ideas, allocate resources, and
provide innovative solutions while understanding
project management practices (Eckhardt, 2018).
Utilizing project management fundamentals can
help them do this.
These skills are particularly important in a
business school, where assessment and
accreditation factors measure course learning
outcomes and course design (Currie, 2017).
Using project management methodology in
curriculum can increase strategic and critical
analysis skills. Students learn and apply
knowledge to gain an appreciation for the
proposed gap between theory and overall
application and include critical thinking and
strategy into their mindset (Dirksen, 2015).
Reducing cognitive load can assist in knowledge
and skill retention and application (Doyle &
Zakrajsek, 2018).
The use of evidence-based pedagogies to inform
practical business application in the classroom
enhances engagement and relevance (Mitchell,
2016), while leveraging the expertise of faculty
and providing structure and support to students
(Dirksen, 2015). Project management skill
development and the use of appropriate tools
provides an opportunity to enhance structure and
application of methodologies that are empirically
supported practices in industry. The integration of
industry skills and problem-based pedagogy
prepares graduates to successfully transition
from the rigor of the academic environment to the
modern expectations of the business world
(Ewing & Ewing, 2017). Linking course learning
outcomes to industry requirements is essential
and should be ongoing in course design (Dirksen,
2015). However, curriculum must continuously
evolve, and this link should be revisited regularly
to address ongoing organizational changes and
industry disruptions while providing an efficient,
cohesive, and holistic structure (Nisula & Pekkola,
2018).
While hands-on, business focused problem
solving that transfers into real world scenarios is
commonplace and expected in the classroom
(Echkardt & Wetherbe, 2016; Ewing & Ewing,
2017), a project-based pedagogy supports
academic rigor in the business curriculum and
provides students with a platform to apply their
program learning as they prepare for the
workplace (McNamara, 2009; Vieregger & Bryant,
2019). Rosenbaum, Otalora, and Ramírez (2015)
suggest that addressing challenges to learning
can be complex and, “although practitioners want
to hire new employees with the ability to solve
real-world problems, a pertinent question to
address is the best method for heeding their
request” (p. 183). Through thoughtfully designed
real-world projects, students can demonstrate
critical thinking and adaptability in evaluating
business problems and determining the most
feasible solutions (Seow et al., 2019).
To develop a curriculum that increases higher-
order thinking, students must be exposed to the
application of how to investigate organizations,
apply knowledge to problem-solving, establish
ideas, and produce creative solutions to problems
identified (Pellegrino & Hilton, 2012). In addition,
encouraging students to organize team projects
using project management methodologies
provides them with the experience to increase
critical thinking and problem-solving skills while
fully investing in learning the course material
beyond just memorization (Kuh, 2008). They
must also have opportunities to reflect on actions
with their team members, which affirms the skills
developed during the learning process and
provides opportunities for critical personal
reflection and enhanced self-awareness (Perusso
et al., 2020). These reflective practices lay the
groundwork for the self-efficacy and change-
making skills necessary for business professionals
(Perusso et al., 2020).
Students that improve project management skills
can identify and address problems as they arise
instead of finding errors at the end. Learning
these skills in an undergraduate business
curriculum will help individuals to become more
proactive and better at decision-making.
Understanding scope management, along with
project management process will help students
with future workplace application (Salapatas,
2000). In addition, communication skills and
enhancement of team dynamics will increase
workplace efficiencies.
Our curriculum integrates consistent project
management tools integrated into each course
project, supporting literature that underscores
the importance of real-world alignment between
course projects and industry standards. For
example, successful project managers seek
support from the Project Management Institute
(PMI) for fundamental, foundational tools and
resources to aid in the execution of projects. PMI
is an international project management

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 7
https://isedj.org/; https://iscap.info
organization that delivers guidelines, resources,
networking opportunities and best practices for
the project management field. Our faculty are
actively engaged in working with PMI to support
the development of experiential learning
activities, exposure to industry speakers, and
providing guidance on careers in the project
management field. In addition, the Project
Management Book of Knowledge (PMBOK) is a
valuable resource that explains the value of
project management structure, guidelines, and
practices. This guide is valuable for faculty to
utilize when enhancing the curriculum and
introducing students to industry standards.
To complement the tools that they are exposed to
while engaging in course projects, we encourage
students to seek professional certifications in
project management, such as the Certified
Associate Project Management (CAPM), and
Project Management Professional (PMP)
certifications offered by PMI. These certifications
tie industry standards to the overall learning
experience. While PMP certifications require
extensive project experience, understanding the
competency requirements can help students to
build project experience and track hours for
future certification testing requirements.
3. PROJECT MANAGEMENT PROCESS
Our aim is to enhance project management-
based learning and curriculum development
across our school. For the project deliverables,
students demonstrate proficiency and the ability
to use credible research to solve ongoing
challenges. We propose that the integration of
project management skill integration, fueled by
innovation and critical strategic analysis, can lead
to an increase in problem-solving capabilities for
students. We monitor learning outcomes within
projects related to problem definition, the
innovation of ideas and challenges, and problem-
solving in business and consulting using an
applied approach.
This paper outlines a structure to integrate
project management processes into course
design. Project management applications in
pedagogical design can further increase effective
collaborations and relationships with industry
leaders and support cross-functional,
interdisciplinary curriculum. Our approach
addresses the needs of employers and the
relevance for graduate application and future
employability.
4. METHODOLOGY
Student Feedback Survey
To determine the level of project management
awareness and skill development present in
undergraduate business students, we collected
online survey data regarding project
management experience and skills from 185
undergraduate students at a medium-sized
private university. No identifying data was
collected, and participation was voluntary.
Students were invited to participate in the survey
via email and recruited from two business core
classes and one senior-level course and included
various majors (e.g., international business,
finance, supply chain, human resources,
accounting, marketing, business analytics,
management, entrepreneurship, CIS, and
business minors with majors from across the
university). Survey items can be found in the
Appendix. 30.3% were first years, 27.6% were
sophomores, 21.1% were juniors, and 21.1%
were seniors. Sixty percent of respondents had
never taken courses or workshops regarding time
management, resource allocation, budgeting, or
project management. Of those who did, 21.8%
had taken only a general introduction. 50.3%
reported wanting to see more project
management content in their courses. When
asked if they were implementing project
management skills such as time management,
scope organization, milestone schedules, risk
management, etc., 55.7% reported they were in
their class projects; 20% said they were in their
student organizations; 10.3% reported they were
in their internships; and 15.7% reported they
were in their jobs. On a Likert scale from 1 (none)
- 6 (expert), 73% of respondents rated a 3 or 4.
When it came to utilizing a project management
charter or contract in their classes, 48.9% had
never used one whereas 75.1% reported using a
project schedule or plan; 76.2% had never used
a project schedule software or tool; and 79.9%
had never used a project scope statement.
Course Design
Our course design methodology is based on the
convincing argument that academia must look at
education from a different mindset, one that can
implement practical applications across multiple
disciplines. Not only do we need to implement
project management consistently throughout our
curriculum, but we must help other disciplines to
see the value. Our unique contribution is to utilize
a consistent experiential approach based on
project work to deliver curriculum consistently
across an entire program. In our approach, we
first identified ways to enhance our courses by
applying project management principles within

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 8
https://isedj.org/; https://iscap.info
course design. Second, our project approach
provides an opportunity to implement the project
management process into undergraduate
education. Third, by recognizing the importance
of skill applicability, there could be an increase in
employability factors relevant for our graduates.
Fourth, we find that project management skill
development provides a realistic, structured
approach to in-class problem-solving that helps
to make solutions real-world feasible.
When building course projects, students should
understand expectations, have clear project
learning goals, and be able to retain foundational
project management skills for future application.
Project planning requirements include developing
an understanding of the scope of work to be
completed. This consists of students
understanding the role that project management
plays in using structure to increase efficiency and
outcomes. To this end, we utilize project-based
assignments that mimic industry workloads and
ask student teams to work with clients preparing
written deliverables and client presentations.
Teams learn the value of documentation of
lessons learned and reflect upon the importance
of understanding team dynamics and execution of
work.
Project Assignment Details
In this section, we provide sample project
descriptions used in our courses to train project
management skills, allowing students to apply
that knowledge in practice.
Project Management Methods
The goals and outcomes of the student's project
work include:
Creating the project team and establishing a team
charter. The team charter identifies rules, norms,
and expectations. The team charter aligns the
project goals with a clear understanding of roles
and points of contact. Best practices could include
insight into the value of the change control
process, use of status reports, or analyzing risk
mitigation plans to keep projects on track.
There is an opportunity to use project
management techniques to create a project plan
and to schedule project activities with
deliverables and due dates. Often scheduling
software can assist with tracking deliverables and
may be covered throughout multiple courses.
Defining the project scope and boundaries
becomes a critical component of the project plan.
While this is not a new practice, understanding
the parameters necessary to keep the scope from
changing will help students value scope
management practice. While our students have
been exposed to the topic of scope management,
many did not appear to retain the introductory
content that was introduced in some of the core
classes.
Students could benefit from analyzing the work
involved in the project plan and integration of a
work breakdown structure (WBS). The WBS can
help students by breaking down tasks associated
with the work and breaking it down into smaller,
more manageable parts of work activities. When
leading projects, using a WBS could help facilitate
a more organized approach to fulfilling the tasks.
Once the project is completed, it is recommended
to review the results and close the project.
Documentation of lessons learned throughout the
project will help with overall project execution in
the future. This data can be stored in a repository
for future project use. We have encouraged our
students to learn from each project experience to
enhance their project leadership potential.
Project Examples:
Introductory Management Project Based
Work
Students participate in management consulting
teams. The teams review assigned businesses
experiencing challenges. Students are evaluated
on their ability to demonstrate knowledge and
evaluation of management philosophies as they
relate to quality indicators such as identifying a
problem or challenge, research of balanced
scorecard, understanding competitors including
benchmarking, and financial statistics outlined in
an executive summary. Framing the problem is
the foundation of the course project and is part of
the project management scope statement. In the
introductory management course, students
review specific company research and metrics by
benchmarking against industry competition.
Students identify the top challenges and outline
research-supported plans to overcome those
challenges.
Operations and Supply Chain Project Based
Work
The project analysis piece in coursework focuses
on identifying and analyzing the supply chain
operations of a particular company. Students
then use data and research to provide managerial
insights. They then apply concepts developed in
class to evaluate and make recommendations.
Students are held accountable using the project
management planning and scheduling tools
outlined above to improve team tasks and

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 9
https://isedj.org/; https://iscap.info
processes. The transferrable skills that are
developed provide a solid foundation for success
in the future.
Senior Seminar Project-Based Work
While students are asked to think critically about
several businesses, they apply their management
program learning outcomes. As students engage
in project-based work, support and direction are
provided by instructors through the course
structure and design, alignment to program
learning outcomes, and the creation of a student-
centered environment for problem-based
learning. The project work uses several smaller
assignments where students recall their learning
to show subject understanding in preparation for
a final real-world project.
Students are given the chance to present their
learning in a presentation requiring student
teams to organize and communicate on a specific
management curriculum subject area. These
areas include forecasting, data analysis for
production demand or inventory control, quality
standard and defect analysis, bottlenecks and
process improvements, product and team
performance issues, ethics compliance, employee
retention, staffing, sourcing, recruitment,
selection, and human resources documentation.
Outcomes
Students are encouraged to think strategically
and critically. Students present their research and
findings to the class including a panel assigned to
be the acting Board of Directors. The research
and application across business disciplines allow
for valuable experiences for students. Alumni
have returned to our classrooms and have shared
evidence that the hands-on curriculum and
project management skills development in our
curriculum helped them to further their career
advancement quickly. Alumni have entered the
workforce prepared to identify challenges,
opportunities for change, and were prepared for
execution.
As supported in the literature, consistency in
project deliverables can assist students in the
retention of the knowledge, skills, and motivation
we are trying to develop. Holding team members
accountable using project management planning
tools and schedules helped to structure team
success and improve team task and interpersonal
processes. Students who engaged with a program
with this practice often demonstrated these
valuable skills. This consistent approach served
as a model for interactions and expectations in
team interactions.
5. DISCUSSION
As evidenced in our survey, not all project
management skills were present in the
undergraduate student population. In fact, the
students that took multiple courses with a specific
project management focus could articulate the
application of the skills and competencies. We
believe that threading project management
throughout multiple courses and majors will
further strengthen this critical skill development
and application.
Survey results suggest that while students are
exposed to project management processes and
techniques, they are not proficient in
implementing standard business practices. The
data demonstrates the value of the integration of
project management practice throughout
undergraduate courses across disciplines. We
cannot fully implement project management
practice and reinforcement without it being
threaded throughout several courses.
Integrating project management tools and
techniques allows students to grow both
academically and professionally in their skill
application. Programs can address the demand
for project management skills, the consistent use
of project management tools and processes in
their pedagogical design of team projects across
courses. When students see that project
management methodologies are used
consistently across courses, they can
continuously hone these skills and improve team
process effectiveness and deliverable outcomes.
When asked to analyze challenges, students must
understand the practical application of problem-
solving, project management techniques and the
consequences of team decisions.
The driver behind our effort has been ongoing
feedback from stakeholders that guide the
process improvement of learning outcomes such
as the demand for graduates with project
management skills. Our applied projects allow
students to link education to increased business
knowledge, improved team dynamics and
communication, critical thinking, and time
management. While we have made progress in
updating the project management curriculum, we
concur that we have not yet fully integrated
project management skill development across the
business curriculum. Our intent is to share the
ideas and thought processes behind the course
design to help others in the development of an
updated project-centric curriculum. While project

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 10
https://isedj.org/; https://iscap.info
management is not a new skill, we feel that it is
highly underutilized and undervalued in the
business education curriculum. We understand
that project management practice continues to
evolve, and educators must continue to enhance
curriculum along this continuum.
Practical Application
We have designed our course assignments and
experiences to be more applicable and
meaningful for our students and their future
employers. A strong body of evidence proposes
integrating feedback from stakeholders and
research theory into each curriculum discussion.
While it is common to offer a project management
curriculum in business schools, integration should
continue to be a thread throughout various
majors. The important development of project
management skills cannot be fully executed in
one or two programs to be successful across the
curriculum. Faculty and practitioners should
continue to stay current with industry trends to
support the development of curriculum and
student outcomes.
Incorporating experiential project-based learning
opportunities, such as student internships and
ongoing project work, should continue to be
included in the curriculum. These experiences will
allow students to apply their project management
skills in an academic and professional setting. In
addition, one of the most effective ways to learn
project management skills is ongoing exposure
and experience participating and leading projects.
By offering more project-based learning
experiences in the undergraduate business
curriculum, you are enhancing the experiences
and applications for your students. In addition, it
would be beneficial across the business
curriculum to identify the pathway to professional
certifications in project management such as
CAPM, while students are completing
undergraduate credits.
Student assessment measures should evaluate
not only the project deliverables but also evaluate
the team process and project management skills.
In each class outlined above, students are held
accountable using project management planning
and scheduling tools to facilitate efficient and
effective team tasks and interpersonal processes.
Team debriefs are also a critical component in
each of our classes to reinforce lessons learned
and continuously improve team processes and
outcomes. Free online tools like ITP Metrics
(https://www.itpmetrics.com/assessment.info)
can help faculty measure team processes and
facilitate team debriefs. Projects should be
experiential in nature and include the application
of key metrics critical for their future success in
the business environment. The project
management tools described outline a
multidisciplinary approach that can be integrated
across business schools and utilized as a platform
to develop an interest in lifelong learning for our
graduates.
Future Consideration
The field of project management is ever-changing
and will continue to evolve. It is important for
educators to stay up to date on the latest best
practices and techniques to ensure that the
curriculum continues to have merit. Partnering
with professional organizations locally such as
PMI (Project Management Institute) can help
ensure this goal will be achieved. Identifying
trends and updating curriculum to address
industry standards and practices will continue to
provide students with lifelong learning
opportunities.
Indeed, exposing students to experiential project
management components has increased
knowledge of factors that are often uncertain,
complex, and unpredictable. Classroom practice
of these factors has better prepared our alumni
for employability as evidenced by our job
placement rates. We continue to monitor insight
from career placement statistics and execute
assignments that allow for practical application.
The outcome of our work is that our students can
walk into an interview with a portfolio of project
deliverables that highlights not just what they
know, but what they can do.
Limitations
We evaluated the course curriculum redesign
within one university. While we believe our
project process is unique in delivering an updated
curriculum, we highlight data from our
introductory management and capstone course
that supports the claim that undergraduate
course curriculum would benefit from
enhancement of project management skills focus.
It would be beneficial to identify best practices in
course design, project management process, and
skill development for future course design
discussions across multiple departments and
various schools, outside of the School of
Business.
6. CONCLUSION
The inclusion of project management tools and
application can increase efficiency in course
design (Echkardt & Wetherbe, 2016). This
pedagogy aligns with AACSB's Impact of
Research Task Force report that argues, "By

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 11
https://isedj.org/; https://iscap.info
bringing together practitioners and academics on
focused topics, education holds enormous
potential to strengthen the linkage between
research and practice" (p. 37). Positioning
graduates with lifelong skills that go well beyond
the traditional classroom setting (Dirksen, 2015).
Experiences using project management
techniques and skills development provide
students with opportunities to enter the
workforce with hands-on experience managing
projects, working with a team, analyzing data,
and applying experiential knowledge (Eckhardt &
Wetherbe, 2016), skill sets relevant to on-the-job
requirements. This prescribed method has not
always been a practice present. Project
management tools can be consistently
implemented across the curriculum to improve
project-based student learning outcomes and
workforce readiness.
7. APPENDIX: STUDENT SURVEY
1. Have you ever taken project
management courses or workshops? If
yes, which methodologies?
a. General introduction
b. Adaptive
c. Agile
d. Kanban
e. Lean
f. PMBOK (Project Management
Book of Knowledge)
g. Prince2
h. Scrum
i. Waterfall/Traditional PM
j. None
k. Other (please specify)
2. Do you have access to project
management professional development
opportunities or training materials?
a. Yes
b. No
c. Unsure
3. Are you familiar with project
management methodologies? If so, select
the ones you are most familiar with:
a. Adaptive
b. Agile
c. Kanban
d. Lean
e. PMBOK
f. Prince2
g. Scrum
h. Waterfall/Traditional PM
i. None
j. Other (please specify)
4. Are you currently implementing any
project management skills, such as time
management, scope organization,
milestone schedules, risk management,
etc.? (Select all that apply)
a. No
b. Yes, in my class projects.
c. Yes, in my student organization.
d. Yes, in my internship.
e. Yes, in my job.
5. If you answered yes, which project
management methodologies are you
currently using?
a. Adaptive
b. Agile
c. Kanban
d. Lean
e. PMBOK
f. Prince2
g. Scrum
h. Waterfall/Traditional PM
i. None
j. Other (please specify)
6. What level of project management skills
do you feel you possess?
a. Likert scale: 1 = none; 6 = expert
7. How confident do you feel managing a
project?
a. Likert scale: 1 = not at all; 6 =
extremely
8. How many class projects have you
participated in during your time as an
undergraduate student?
9. In those class projects:
a. Did you utilize a project
management charter or contract?
i. Yes
ii. No
b. Did you utilize a project
schedule?
i. Yes
ii. No
c. Did you utilize a project schedule
software or tool?
i. Yes
ii. No
d. did you complete a scope
statement?
i. Yes
ii. No
10. Do you consider any of the following
communications, risk, resource, or
quality management at any level when
working on your class projects?
a. Yes
b. No
8. REFERENCES
Final Report of the AACSB International Report
Impact of Research. AACSB International.
Retrieved from https://www.aacsb.edu/-

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 12
https://isedj.org/; https://iscap.info
/media/publications/research-
reports/impact-of-research.pdf
Currie, G. (2017). The social value of translational
research. BizEd AACSB International.
Retrieved from
https://bized.aacsb.edu/articles/2017/09/th
e-social-value-of-translational-research
Daniel, D. B. (2012). Promising principles:
Translating the science of learning to
educational practice. Journal of Applied
Research in Memory and Cognition, 1, 251-
253.
Doyle, T., & Zakrajsek, T. (2018). The new
science of Learning: How to learn in harmony
with your brain (2
nd
Ed). Sterling, VA: Stylus
Publishing.
Dirksen, J. (2015). Design for how people learn
(2
nd
ed.). New Riders.
Eckhardt, J. (2018). James Wetherbe: How
consulting connects colleges to the real world.
Entrepreneurship & Innovation Exchange.
Retrieved from
https://eiexchange.com/content/360-James-
Wetherbe-how-consulting-connects-colleges
Eckhardt, J., & Wetherbe, J. (2016, February 9).
Connecting business research to practice.
Entrepreneurship & Innovation Exchange.
Retrieved from
https://eiexchange.com/content/126-
connecting-business-research-to-practice
Ewing, D. R., & Ewing, R. L. (2017). Leveraging
Experiential Learning to Encourage Role
Transition From “Student” to “Professional”:
Insights From Identity Theory. Journal of
Marketing Education, 39(3), 132–144.
https://doi.org/10.1177/0273475317724844
Gharaie, E., & Wingrove, D. (2020). Strategies for
effective teaching in project management. In
S. Mostafa, & P. Rahnamayiezekavat (Ed.),
Claiming Identity Through Redefined
Teaching in Construction Programs (pp. 197-
223). IGI Global.
https://doi.org/10.4018/978-1-5225-8452-
0.ch011
Karanja, E. & Grant, D. M. (2020). Evaluating
learner-centeredness course pedagogy in
project management syllabi using a content
analysis approach. Journal of Information
Systems Education, 31(2), 131-146
Kuh, G. D. (2008). High-impact educational
practices: A brief overview. Association of
American Colleges and Universities. Retrieved
from www.aacu.org/leap/hips
Martin, F. & Bolliger, D.U. (2018). Engagement
matters: Student perceptions on the
importance of engagement strategies in the
online learning environment. Online Learning
22(1), 205- 222.
doi:10.24059/olj.v22i1.1092
McNamara, B. R. (2009). The skill gap: will the
future workplace become an abyss.
Techniques: Connecting Education and
Careers, 84(5), 24-27.
Morrison, G. R., Ross, S. M., & Kemp, J. E.
(2006). Designing effective instruction (5
th
ed.). Jossey-Bass, Wiley.
Mitchell, P. (2016) From concept to classroom.
Australian Council for Educational Research.
Retrieved from
https://research.acer.edu.au/cgi/viewconten
t.cgi?article=1009&context=professional_de
v
Nisula, K., & Pekkola, S. (2018), How to move
away from the silos of business management
education? Journal of Education for Business,
93(3), 97-111. doi.
10.1080/08832323.2018.1425283
Pellegrino, J. W., & Hilton, M. L. (Eds.). (2012).
Education for life and work: Developing
transferable knowledge and skills in the 21st
century. Washington, DC: The National
Academies Press.
Perusso, A., Blankesteijn, M., & Leal, R. (2020).
The contribution of reflective learning to
experiential learning in business education.
Assessment and Evaluation in Higher
Education, 45(7), 1001–1015.
https://doi.org/10.1080/02602938.2019.17
05963
Rocca, K. A. (2010). Student participation in the
college classroom: An extended
multidisciplinary literature review.
Communication Education, 59(2), 185-213.
doi:10.1080/03634520903505936
Rosenbaum, M., Otalora, M., & Ramírez, G.
(2015) Promoting problem-based learning in
retailing and services marketing course
curricula with reality television. Journal of
Education for Business, 90(4), 182-191.
doi:10.1080/08832323.2015.1014456
Salapatas, J. N. (2000). Best practices—the nine
elements to success. Paper presented at
Project Management Institute Annual
Seminars & Symposium, Houston, TX.
Newtown Square, PA: Project Management
Institute.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 13
https://isedj.org/; https://iscap.info
Seow, P.-S., Pan, G., & Koh, G. (2019).
Examining an experiential learning approach
to prepare students for the volatile,
uncertain, complex, and ambiguous (VUCA)
work environment. The International Journal
of Management Education, 17(1), 62–76.
https://doi.org/10.1016/j.ijme.2018.12.001
Thai, N. T. T., De Wever, B., & Valcke, M. (2017).
The impact of a flipped classroom design on
learning performance in higher education:
Looking for the best “blend” of lectures and
guiding questions with feedback. Computers
& Education, 107, 113-126.
Vandenhouten, C., Groessl, J., & Levintova, E.
(2017). How do you use problem‐based
learning to improve interdisciplinary thinking?
New Directions for Teaching and Learning,
2017(151), 117-133. doi: 10.1002/tl.20252
Vieregger, C., & Bryant, A. (2019). Student-
alumni mentoring in the business capstone:
An opportunity to both cap and bridge the
undergraduate experience. Journal of
Education for Business, 1-9. doi:
10.1080/08832323.2019.1646700

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 14
https://isedj.org/; https://iscap.info
Enforcement of Prerequisites in Computer Science
Ernst Bekkering
Patrick Harrington
Mathematics and Computer Science
Northeastern State University
Tahlequah, OK 74464
Abstract
This paper describes the study of enforcement of prerequisites in the Computer Science program at a
regional university in the Southwest. Prerequisites are a significant factor in programs of study in higher
education. Allowing students to register in courses may assume that they have existing knowledge and
skills. Some programs treat prerequisites as advisory, while others consider them mandatory. In the
latter case, procedures usually exist to make exceptions in the form of registration overrides. The state
of prerequisite enforcement at our university over the years, and some factors that may have influenced
adherence to the prerequisite structure over the years, will be discussed in this paper.
Keywords: enrollment, curriculum, prerequisites, scheduling, graduation.
1. INTRODUCTION
In higher education, courses may have
prerequisites and/or co-requisites to ensure that
students taking the course are sufficiently
prepared. In reality, enforcement of these
prerequisites may be difficult. For instance,
enrollment systems cannot check prerequisites
until after the semester end because course
grades have not been awarded and enrollment for
the next semester starts well before the current
semester ends (Boyer & Bucklew, 2019). A
variety of processes exist to deal with this timing
problem.
The issue of enforcing prerequisites is especially
important when the demand for a course exceeds
the course capacity. Students who should not be
taking the course (yet) take a seat that should
have gone to students who do qualify (Soria &
Mumpower, 2012).
This research will examine the compliance with
successful completion of prerequisites and
enrollment in co-requisites in the Computer
Science program where the investigators teach.
The paper is organized as follows. In the next
section, we discuss the relevant literature. Next,
we discuss the methodology of our study, data
collection, and data analysis. We end with
conclusions and recommendations.
2. LITERATURE REVIEW
Prior knowledge and skills needed to be
successful in a course can take multiple forms.
Prerequisites can be defined as courses or tests
that must be successfully completed prior to
registering for the target course. In some cases,
special tests are given at the start of a course to
identify students who need additional support to
get caught up. Co-requisites are courses that
must be taken at the same time as another
course. In the case of labs partnered with lecture
sections, the reason for the split is usually
administrative – multiple lab sections with fewer
students are needed to give all students sufficient
individual attention in the lab. In other cases, the
material in one course is supportive of the target
course. For instance, Discrete Mathematics may

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 15
https://isedj.org/; https://iscap.info
be co-requisite for Basic Computer Architecture to
cover Boolean logic more in-depth in the
mathematics course.
Rationale for expecting prior knowledge
Curriculum design involves combining multiple
courses into an integrated program of study.
Considering limitations of time and other
resources, programs should maximize coverage
of content while minimizing overlap. As Diamond
(1998) states:
“One of the most prevalent problems in
course and curriculum design is the tendency
of faculty to make false assumptions about
the knowledge and skills that students bring
to their courses. These incorrect assumptions
lead to failure for the students who are ill
prepared, boredom for their classmates who
are often more than adequately prepared,
and frustration for the faculty.”
Performance in advanced courses depends on
how the material in prerequisite courses is used
and evaluated (Nelson et al., 2020). Lack of
correct prerequisites and lack of continuity
between courses in a sequence are specifically
mentioned as causes of student failure (Babb et
al., 2014). “Depth of knowledge” assumes a
hierarchical structure of programs (Reynolds et
al., 2016). This is not limited to a single program
of study. If programs have more than one
concentration, two or more sequenced courses
within the concentration are required (Downey et
al., 2008).
Babb et al. (2014) propose that students must
“step-wise and incrementally, engage in the
persistent and iterative pursuit of programming”
of at least 15 out of 23 topics over the course of
the curriculum. Longenecker et al. (2013)
suggest a series of three programming courses
with database as prerequisite for the last course.
Decreasing the number of programming courses
in the early 2000s backfired, and industry
continues to demand technical skills (George &
Marett, 2019).
Prerequisites do not come without drawbacks.
Students can suffer delays in graduation, and
universities may have to offer more courses with
a deeper prerequisite structure (Reynolds et al.,
2016). For some students, it can be a reason to
select another major (Li et al., 2014). It is
therefore important to impose only prerequisites
that are necessary and effective.
Effectiveness
Much of the research on prerequisites has focused
on their effectiveness in a program’s curriculum.
The effect of prior knowledge has been tested
statistically through correlation of prior
coursework and final grades in the target course,
and by correlation with special pretests at the
start of the target course.
Examples of studies that use final grades in the
target course are Blaylock & Lacewell (2008),
Krause-Levy et al. (2020), Liao et al. (2019), and
Soria & Mumpower (2012). All found positive
relationships between prerequisites and target
courses.
Passing previous courses may not be effective.
The use of proficiency tests instead of
prerequisite courses has been described by
Rondeau & Li (2009). Instituting the test created
a backlog of students who failed the test, and the
test did not fully cover the required knowledge.
Also, not all prior knowledge can be obtained in a
single course. Blaylock & Lacewell (2010) used a
prerequisites test covering topics from multiple
disciplines to demonstrate that prior knowledge
led to better final grade results. Sargent (2013)
used proficiency tests for Intermediate
Accounting with good result. Abou-Sayf (2009)
concluded that using entrance tests in the target
course provided more accurate results than using
final grades.
Higher education has become increasingly fluid.
Whereas decades ago, students tended to
complete degrees in one institution, the last
decade has seen an increasing number of
students who transfer from community colleges
to four-year institutions to finish their degree.
Transfer agreements between schools and state
transfer guides (for instance OSRHE (2022)) help
students to combine courses from multiple
sources into a single degree. Needless to say, this
assumes sufficient similarity of course contents to
be successful. The effect of transfer guides on the
number of prerequisites taken elsewhere is small,
and mature students benefit more (Spencer,
2019). Furthermore, Catanese et al. (2018) found
no significant difference in a third computing
course between native students and transfer
students who took the first two courses
elsewhere.
Finally, some problems exist in quantitative
measurement of the effect of prerequisites.
Students are more mature in the target course,
the students in the prerequisite and target course
partially overlap, self-selection happens due to
students not following up with the target course,

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 16
https://isedj.org/; https://iscap.info
and a cause-and-effect relationship has not been
demonstrated (Abou-Sayf, 2009).
Selection process
The second main area for prerequisites research
is in the selection process. One of the first
questions in delivering courses is the issue of
prerequisite knowledge (Johnson et al., 2002). In
some cases, this is easy. Database II should have
Database I as direct prerequisite (Reynolds et al.,
2016). Computer Science II should be preceded
by successful completion of Computer Science I,
and Object-Oriented Programming (in Java)
might need the coverage of objects in C++. Model
curricula may suggest this type of sequential
prerequisites. In IS2010 and IS2020,
Foundations of Information Systems is
prerequisite for most other courses, and all other
courses must be passed before culminating
courses like the capstone course (Leidig et al.,
2019; Leidig & Salmela, 2021).
Other prerequisites may be less intuitive. Some
courses have non-sequential prerequisites from
other disciplines. For instance, some
programming courses may need the logical
thinking from specific Mathematics courses.
White found that prerequisites are needed to
develop the proper cognitive style in order to be
successful in Visual Basic programming (2012).
In a follow-up study, White and Sivitanides
suggested that freshman level mathematics
courses are good indicators for success in Visual
Basic (2003). To fully understand the issues
round technology-based entrepreneurship, a
course on information systems in business is
essential (Jones & Liu, 2017).
Level of enforcement
Registration systems contribute to the problem of
skipping prerequisites (Wilkerson et al., 2019). As
mentioned before, course registration systems
have difficulty enforcing prerequisites if
registration for a future semester is allowed
before grades in the current semester have been
posted. Several solutions to this dilemma exist.
First, universities may use conditional enrollment
pending successful completion of the
prerequisite. Second, appropriate staff can issue
overrides. Academic advisors may have
permission to issue an override if transfer courses
have not been posted in the transcript system
yet, and faculty may override enrollment blocks
in courses they teach if they deem the
prerequisite unnecessary for specific students.
Departments can give overrides for courses in
their department. An example of this process can
be found at OSU (2021) . Third, enrollment
without prerequisites may not be blocked. Course
descriptions may merely mention prerequisites,
and students can not notice or ignore them. In
that case, it would be up to faculty to check
transcripts before or at the start of the course.
Finally, the university may only open enrollment
after grades in the current semester have been
posted. This pushes enrollment back compared
with early registration and is unattractive from an
administrative point of view. Soria & Mumpower
(2012) describe their university’s switch to an
automated, mandatory prerequisite enforcement
system and found that it led to better academic
outcomes.
The need to check grades does not exist for co-
requisites. If the course has been taken before it
is available in the transcript system, and if not
must be taken in the same semester as the
target course. Registration systems could check if
the co-requisite is covered and either disable
registration until it is met or issue a warning that
the co-requisite course must also be registered.
In closing, student compliance with prerequisites
and co-requisites is a multi-faceted issue. The
literature indicates that they are effective, gives
some guidelines for their selection, and that they
may not always be followed. We have not been
able to find literature indicating how often they
are skipped, and that is the focus of this study.
3. METHODOLOGY
This section describes the methodology of
measuring compliance with successful completion
of prerequisites and enrollment in co-requisites
for the Computer Science program.
Online university systems
Students register on Banner and transcripts can
be checked on DegreeWorks.
Course registration system
The Banner system (Ellucian Company LP, 2022a)
is a comprehensive suite that includes student
course registration and instructor functions like
generating course enrollment listings and grade
entry. Enrollments are synchronized nightly with
the course management system BlackBoard. The
gradebooks in BlackBoard contain the student
identifiers for each course.
Registration overrides may be customizable by
the university, allowing different users and
groups different permissions. At our university,
overrides for undergraduate courses can be
issued by faculty, department, and academic
advisors (Figure 1). Prerequisites are not listed as

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 17
https://isedj.org/; https://iscap.info
a reason. Academic advisors contact faculty for
prerequisite overrides. This typically happens
between Software Engineering and its target
Capstone course.
Figure 1 - Types of overrides
Transcript system
DegreeWorks (Ellucian Company LP, 2022b)
allows selecting single students based on their N
number (a unique number unconnected with
other identifiers such as social security numbers)
but also has a search function that includes
searching on majors and minors. The results of
each search are displayed in a popup window with
name and N numbers.
The frequency of synchronization between grade
entry on the Banner system and the transcripts in
Degreeworks is not known but assumed to be
frequent since both packages are sold by the
same company. The “historic audit” dropdown
shows multiple snapshots during the semesters,
and the “date refreshed” field can be used to
refresh the current transcript on the fly.
Transcripts show all required courses for the
program of study, the semester when taken or
scheduled, the course grade status, and special
notes for course transfers and substitutions.
Sample (anonymized) transcripts for are shown
in Appendix A.
Prerequisites in the CS program
The Computer Science program has multiple
courses with prerequisites or co-requisites. Some
are sequential, such as Computer Science I and
Computer Science II which even use the same
textbook. Other courses are non-sequential, such
as Object Oriented Programming and Software
Engineering. The course content in the
programming course is not used directly in the
target course, but the intent is to ensure that
students have sufficient programming
background to start preparing for the Capstone
course. A complete listing of common courses
with prerequisites is provided in Table 1. Some
courses with prerequisites in the course catalog
are seldom or never offered, and we ignored
those. We also omit courses restricted to
instructor permission only.
Course
Prerequisite/co-requisite
CS 2014
Computer
Science I
Applied Mathematics (co) or
College Algebra (co) or
ACT >=23
and computer proficiency
CS 2163
Computer
Science II
Computer Science I with C
minimum
CS 3033
Object
Oriented
Programming
Computer Science I with C
minimum
CS 3173
Basic
Computer
Architecture
Computer Science II (co)
and
MATH 3023 Discrete
Mathematics (co)
CS 3343
Computer
Operating
Systems
Basic Computer Architecture
CS 3403
Data
Structures
Computer Science II with C
minimum and
MATH 3023 Discrete
Mathematics
CS 4343
Database
Management
Systems
Computer Science II and
MATH 3023 Discrete
Mathematics
CS 4203
Software
Engineering
Object Oriented
Programming with C
minimum
CS 4233
Capstone
Software Engineering
Table 1 - Courses and prerequisites
Based on prerequisites in required courses, the
program has a critical path to graduate in four
semesters after General Education requirements
have been met. The critical path is shown in
Figure 2. In all three versions, completing the
upper division courses in four semesters is only
possible with the sequenced prerequisites
Computer Science I, Object Oriented
Programming, Software Engineering, and
Capstone (Professional Development in CS).
This critical path was shortened about six years
ago. Before the change, the prerequisite for
Object Oriented Programming was Computer
Science II, not Computer Science I. The critical
path at that time had a length of five courses with
Computer Science I, Computer Science II, Object

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 18
https://isedj.org/; https://iscap.info
Oriented Programming, Software Engineering,
and finally the capstone course. Even though we
felt that Computer Science II was a better
prerequisite for Object Oriented Programming
than Computer Science I, we decided to shorten
the path. This demonstrates that some of the
considerations in the use of prerequisites are
political as noted by Abou-Sayf (2009).
Figure 2 - Critical Path in CS
Course rotation
The CS program is offered on two campuses. In
the past, courses were only offered face to face
(f2f) on alternating campuses. With the advent of
powerful online meeting tools like BlackBoard
Collaborate and later Zoom, courses were
increasingly split in two sections, with one section
f2f and the other online concurrently. This allowed
students to take courses each semester
independent of their main campus, and the
course rotation is shown in the first image in
Appendix B.
Starting with the Fall 2021 semester, the course
offerings were reduced to once a year, regardless
of campus. Faculty could select the campus for
the f2f section and stream the course to the other
campus. The faculty with doctoral degrees were
reduced from five to three by releasing two
faculty on the tenure track and not replacing
them. The road map with implicit course rotation
is shown in the second image in Appendix B.
The road map for CS shows that CS courses are
spread over four years and eight semesters. In
our program, approximately half of the CS majors
complete all four years at our university, but the
other half consists of transfer students from
community colleges. For those transfer students,
and students who do not declare CS as their
major until after completion of their General
Education courses, students can combine the
major and minor courses for the first and second
years in the appropriate semesters, as well as

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 19
https://isedj.org/; https://iscap.info
combining the third and fourth years. For all
students though, most of the required courses are
offered only once a year. This complicates proper
course selection for our majors.
Scraping web data
All course registration data and all transcripts are
accessible online at the university website. One of
the current popular tools for collecting online data
is a combination of the Python programming
language and the Selenium module to automate
user actions in web browsers (Chapagain, 2019).
The Scrapy module (Zyte, 2022) is faster due to
multithreading but does not render JavaScript
and is not very user-friendly. BeautifulSoup
(Richardson, 2015) needs additional modules for
sending requests and parsing HTML pages.
Selenium is easy to use, sends its own requests,
and can pull data that is only available when
JavaScript is loaded (Grimes, 2022).
4. DATA COLLECTION
We filtered the transcript system on Computer
Science majors and copied the list of students to
a text file. Student identification numbers are in
the format Nxxxxxxxx, where x is a digit. The N
numbers were extracted with regular
expressions, and we used Python scripts with
Selenium to download transcripts and test scores.
Transcripts and test scores were saved with
corresponding random numbers for file names
and identifying information in the files was
removed. Finally, we used Python scripts with
Selenium and BeautifulSoup to extract the data
we needed in csv format.
The csv file was used as the data source for the
analysis spreadsheet. Separate tabs for each
course reviewed extracted the data for the
prerequisites and co-requisites and used lookup
tables to convert semesters to sequential
numbers. The semester numbers of prerequisites
and co-requisites were compared with the
number of the target course to check if they fell
before or with the target course and stored in
true/false format. Separate lookup tables were
used to check for passing grades in prerequisites
and co-requisites and stored in true/false format.
Formulas with AND() and OR() were constructed
to check if all rules were met.
We filtered first on target courses being taken,
and then on meeting all the rules. Finally, we
assigned categories for the reasons. Figure 3
shows an example for Basic Computer
Architecture, which has two co-requisites with
passing grades of D.
Figure 3 - Categorization
Finally, the data were summarized on a separate
tab by semester and categories in tabular and
graphical format for analysis.
5. ANALYSIS AND DISCUSSION
We will now discuss the CS major courses. We will
start with a brief description of the course and its
requirements, followed by the results and our
interpretation. Appendix C shows graphs for the
number of times requirements were not met, the
occurrences relative to the total times the course
was taken in the semester, and a breakdown of
the reasons. The historical rate mentioned is the
rate of unmet requirements over the history of
the program, based on all available transcripts.
Computer Science I is the introductory
programming course. The course presents the
basics of programming in C++. Two Math courses
can be taken as a co-requisite, or students can
qualify with an ACT of 23 or higher. All students
must have computer proficiency. The course has
a substantial number of students who do not
meet the requirements. The historical rate is
17.8%. One of the prerequisites is usually taken
before the course, but a substantial number of
students fail the MATH course. The main reason
for failing the requirements is not taking them,
with a strong second not passing when taken
before. Very few students fail to get a passing
grade when taken concurrently.
Computer Science II presents more programming
in C++. In contrast to Computer Science I, it has
a low historical rate of 4.1%. The course has
Computer Science I with a minimum of C as a
prerequisite. The majority of students not
meeting it are transfer students from a
Community College who either failed to get a C or
took the courses concurrently.
Object Oriented Programming is taught in Java.
The prerequisite is Computer Science II, which
has to be passed with a C. The historical rate is
extremely low at 2.5%, with more than half
related to transfer students who fail to get a C or
taking the prerequisite late.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 20
https://isedj.org/; https://iscap.info
Basic Computer Architecture presents the
theoretical foundation of computers, including the
basic hardware components and an introduction
to assembly language. It has two courses that can
be taken before or concurrently. The historical
rate is 11.5%. About twice as many students fail
to pass Discrete Mathematics as Computer
Science II.
Computer Operating Systems follows Basic
Computer Architecture, its only prerequisite. The
course presents topics like concurrency,
processes, and threads. The historical rate is
lower at 7.9%. Both courses are taught in
opposite semesters and taking the prerequisite
two semesters later generally delays graduation.
Data Structures introduces both common data
structures and algorithms used in Computer
Science. The historical rate is 8.6%, of which
more than three quarters is caused by not passing
Discrete Mathematics and the rest by failing to
pass Computer Science II or both.
Database Management Systems presents
multiple forms of databases as storage and
retrieval tools for data. It has a historical rate of
10.8%, with two thirds due to not meeting the
Discrete Mathematics requirement and one third
not passing Computer Science II.
Software Engineering presents the software
development process including requirements
analysis, modeling, and testing. Combining this
course with previous programming courses
prepares the students for the integrative
Capstone course. The historical rate is higher
again at 14.7%, with only a very minor part due
to failing the prerequisite. The remainder is
evenly split between taking the courses
concurrently and taking the prerequisite after the
software engineering course.
The capstone course has students develop an
individual integrative project of their choice. The
historical rate for not meeting the Software
Engineering prerequisite is 16.0%, with virtually
all due to taking the capstone and its prerequisite
concurrently.
Table 2 presents a summary of the historical rate
of unmet requirements. The rate appears to vary
based on three factors. First, courses with
Mathematics prerequisites tend to have higher
rates. This is true for especially Computer Science
I. Second, sequential courses tend to have lower
rates. This is true for Computer Science I and II
(4.1%), Computer Science I and Object Oriented
Programming (2.5%), and Basic Computer
Architecture and Computer Operating Systems
(7.9%). Finally, courses later in the program tend
to have higher rates. We attribute this to the
pressure to graduate on time.
Course
Sequential
Percent
Unmet
Computer Science I
no
17.8%
Computer Science II
yes
4.1%
Object Oriented
Programming
yes
2.5%
Basic Computer
Architecture
no
11.5%
Computer Operating
Systems
yes
7.9%
Data Structures
no
8.6%
Database
Management
Systems
no
10.8%
Software
Engineering
no
14.7%
Capstone
no
16.0%
Table 2 - Historical Rate of Unmet
Requirements
6. CONCLUSIONS AND RECOMMENDATIONS
Our analysis shows a significant level of failing to
meet requirements for courses in our Computer
Science program. As involved faculty members,
the results do not surprise us. We do see this as
an opportunity to take actions that alleviate this
problem.
The tools used for this study can be converted to
multiple proactive tools. We can generate lists for
academic advisors with students needing to take
the specific courses in the following semester.
These lists can be used in advising sessions, to
contact students proactively by email or text
message, and to check courses needed against
actual enrollments. The same lists can be used by
the department to estimate demand for the next
semester so an adequate number of course
sections can be scheduled. Finally, we can
generate faculty lists with checked prerequisites
and co-requisites at the start of the semester to
maximize the enrollment of eligible students by
eliminating non-eligible students.
Finally, our study does not address the effect of
unmet prerequisites on student performance in
the target course. We plan to make this a
separate study.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 21
https://isedj.org/; https://iscap.info
5. REFERENCES
Abou-Sayf, F. K. (2009). Challenges inherent in
the assessment of the impact of prerequisite
courses. Journal of Applied Research in the
Community College, 17(1), 9–15.
Babb, J. S., Longenecker, B., Baugh, J., &
Feinstein, D. (2014). Confronting the Issues
of Programming In Information Systems
Curricula: The Goal is Success. Information
Systems Education Journal, 12(1), 42.
Blaylock, A., & Lacewell, S. K. (2008). Assessing
Prerequisites as a Measure of Success in a
Principles of Finance Course. Academy of
Educational Leadership Journal, 12(1), 51–
62.
Blaylock, A., & Lacewell, S. K. (2010). Ex Ante
Prerequisite Knowledge and Student Success
in Principles of Finance. Journal of Learning in
Higher Education, 6(1).
Boyer, N., & Bucklew, K. (2019). Competency-
based education and higher education
enterprise systems. The Journal of
Competency-Based Education, 4(1), e01180.
https://doi.org/10.1002/cbe2.1180
Catanese, H., Hauser, C., & Gebremedhin, A. H.
(2018). Evaluation of native and transfer
students’ success in a computer science
course. ACM Inroads, 9(2), 53–57.
https://doi.org/10.1145/3204471
Chapagain, A. (2019). Hands-On Web Scraping
with Python: Perform advanced scraping
operations using various Python libraries and
tools such as Selenium, Regex, and others.
Packt Publishing Ltd.
Diamond, R. M. (1998). Designing and Assessing
Courses and Curricula: A Practical Guide.
Second Edition. The Jossey-Bass Higher and
Adult Education Series. Jossey-Bass, Inc.
Downey, J. P., McMurtrey, M. E., & Zeltmann, S.
M. (2008). Mapping the MIS Curriculum
Based on Critical Skills of New Graduates: An
Empirical Examination of IT Professionals.
Journal of Information Systems Education,
19(3), 351.
Ellucian Company LP. (2022a). Banner ERP
System for Universities. Ellucian.
https://www.ellucian.com/solutions/ellucian-
banner
Ellucian Company LP. (2022b). Ellucian Degree
Works. Ellucian.
https://www.ellucian.com/solutions/ellucian-
degree-works
George, J. F., & Marett, K. (2019). The Times they
are a Changin’: How Non-Technology Factors
have Affected IS Curriculum over Time.
Journal of Information Systems Education,
30(4), 222.
Grimes, J. (2022, March 27). Scrapy Vs.
Beautifulsoup Vs. Selenium for Web Scraping.
Best Proxy Reviews.
https://www.bestproxyreviews.com/scrapy-
vs-selenium-vs-beautifulsoup-for-web-
scraping/
Johnson, D. W., Wilkes, F., Ormond, P., &
Figueroa, R. (2002). Adding Value to the
IS’97… Curriculum Models: An Interactive
Visualization and Analysis Prototype. Journal
of Information Systems Education, 13(2),
135.
Jones, C. G., & Liu, D. (2017). Approaches to
Incorporating IT Entrepreneurship into the
Information Systems Curriculum. Journal of
Information Systems Education, 28(1), 43.
Krause-Levy, S., Valstar, S., Porter, L., &
Griswold, W. G. (2020). Exploring the Link
Between Prerequisites and Performance in
Advanced Data Structures. Proceedings of the
51st ACM Technical Symposium on Computer
Science Education, 386–392.
https://doi.org/10.1145/3328778.3366867
Leidig, P., Ferguson, R., & Reynolds, J. (2019).
IS2010: A Retrospective Review and
Recommendation. Journal of Information
Systems Education, 30(4), 298–302.
Leidig, P., & Salmela, H. (2021). IS2020 Final
Report – IS2020 ACM-AIS Curriculum.
https://is2020.hosting2.acm.org/2021/06/0
1/is2020-final-draft-released/
Li, L., Zhang, C., & Zheng, G. (2014). Promoting
Information Systems Major to Undergraduate
Students—A Comprehensive
Investigation</title>. Journal of Information
Systems Education, 25(3), 211.
Liao, S. N., Zingaro, D., Alvarado, C., Griswold,
W. G., & Porter, L. (2019). Exploring the
Value of Different Data Sources for Predicting
Student Performance in Multiple CS Courses.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 22
https://isedj.org/; https://iscap.info
Proceedings of the 50th ACM Technical
Symposium on Computer Science Education,
112–118.
https://doi.org/10.1145/3287324.3287407
Longenecker, H. E., Feinstein, D. L., & Babb, J. S.
(2013). Is there a need for a Computer
Information Systems model curriculum.
Proceedings of the Information Systems
Educators Conference ISSN, 2167, 1435–
1447.
Nelson, G. L., Strömbäck, F., Korhonen, A.,
Begum, M., Blamey, B., Jin, K. H., Lonati, V.,
MacKellar, B., & Monga, M. (2020).
Differentiated Assessments for Advanced
Courses that Reveal Issues with Prerequisite
Skills: A Design Investigation. Proceedings of
the Working Group Reports on Innovation and
Technology in Computer Science Education,
75–129.
https://doi.org/10.1145/3437800.3439204
Oklahoma State University. (2021, October 26).
Banner Registration Permits/Overrides for
Faculty and Staff—Oklahoma State
University.
https://registrar.okstate.edu/banner-
registration-permits-overrides-faculty-
staff.html
OSRHE. (2022). Oklahoma State Regents for
Higher Education | Students | Transfer
Students | Course Transfer.
https://www.okhighered.org/transfer-
students/course-transfer.shtml
Reynolds, J., Ferguson, R., & Leidig, P. (2016). A
Tale of Two Curricula: The Case for
Prerequisites in the Model Curriculum.
Information Systems Education Journal,
14(5), 17.
Richardson, L. (2015). Beautiful Soup
Documentation—Beautiful Soup 4.4.0
documentation. https://beautiful-soup-
4.readthedocs.io/en/latest/
Rondeau, P. J., & Li, X. (2009). The Impact of a
Computer Proficiency Exam on Business
Students’ Admission to and Performance in a
Higher-Level IT Course. Journal of
Information Systems Education, 20(4), 477.
Sargent, C. S. (2013). Find it, fix it, and thrive:
The impact of insisting on proficiency in
prerequisite knowledge in intermediate
accounting. Issues in Accounting Education,
28(3), 581–597.
Soria, K. M., & Mumpower, L. (2012). Critical
Building Blocks: Mandatory Prerequisite
Registration Systems and Student Success.
NACADA Journal, 32(1), 30–42.
Spencer, G. (2019). Can Transfer Guides Improve
the Uptake of Major Prerequisites? Evidence
from Ohio’s Transfer and Articulation Policy
Reform. Research in Higher Education, 60(4),
458–484. https://doi.org/10.1007/s11162-
018-9522-2
White, G. (2012). Visual Basic Programming
Impact on Cognitive Style of College
Students: Need for Prerequisites. Information
Systems Education Journal, 10(4), 74.
White, G., & Sivitanides, M. (2003). An Empirical
Investigation of the Relationship Between
Success in Mathematics and Visual
Programming Courses. Journal of Information
Systems Education, 14(4), 409.
Wilkerson, J. M., Palmer, D. W., & Meyer, J. C.
(2019). Disintegrating Business Degree
Curricula by Skipping Prerequisite Courses.
Journal for Excellence in Business &
Education, 6(1), Article 1.
http://www.jebejournal.org/index.php/jebe/
article/view/113
Zyte. (2022). Scrapy | A Fast and Powerful
Scraping and Web Crawling Framework.
https://scrapy.org/

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 23
https://isedj.org/; https://iscap.info
Appendix A – Sample anonymized transcripts
Graduated student

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 24
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 25
https://isedj.org/; https://iscap.info
Ongoing student

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 26
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 27
https://isedj.org/; https://iscap.info
Appendix B – Course rotations

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 28
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 29
https://isedj.org/; https://iscap.info
Appendix C – Results by Course

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 30
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 31
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 32
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 33
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 34
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 35
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 36
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 37
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 38
https://isedj.org/; https://iscap.info
Mid-Pandemic Impact on
Mobile Learning Motivation Factors
Neelima Bhatnagar
University of Pittsburgh
Greensburg, PA 15601 USA
Ann-Marie Horcher
Northwood University
Midland, MI 48642 USA
Abstract
The study examines the motivating factors driving mobile information systems use (MISU) for mobile
learning. The primary objectives include comparing attitudes of students and faculty towards the
influence of perceived usefulness (PU), perceived playfulness (PP), and perceived enjoyment (PE) on
MISU. Additionally, the influence of personal innovativeness (PI) on PU, PE, and PP is also assessed. The
previous study examined these attitudes prior to the pandemic. This study focuses on the attitudes
existing mid-pandemic, when new strategies toward m-learning were by necessity applied much more
broadly than at any other time historically. The method used is a survey of quantitative constructs.
Research contributions, limitations, and implications for future research are also discussed. Though
student participants felt perceived usefulness led to mobile learning use mid-pandemic, faculty did not.
Furthermore, neither group felt perceived usefulness yielded perceived usability.
Keywords: motivation, mobile learning, pandemic, m-learning, COVID-19
1. INTRODUCTION
Organizations of all types have benefited from the
development and use of information systems
("Measuring Digital Development Facts and
Figures 2021," 2021). With the explosion of
mobile applications, also known as mobile
information systems, new uses are emerging.
One such application of mobile information
systems is mobile learning, referred to as m-
learning hereafter. M-learning has found its ways
in the corporate world for employee training and
development, and in higher education for
teaching and student learning. However, m-
learning has historically not seen the same extent
of usage as distance learning and e-learning,
often attributed to technological limitations.
Motivational factors, though, may also contribute
to the slow adoption of m-learning. But
quarantine on a global scale produced a new level
of motivation. With schools no longer in person,
participation in learning required online
interaction. If the problems of m-learning usage
are not well understood and addressed, then
usage may possibly decrease and the
opportunities inherent in m-learning may be
missed. Extant literature includes numerous m-
learning studies explicitly focused on student use
and perceptions of m-learning. Faculty members,
on the other hand, have not been the focus of
many studies, despite the integral role that
faculty motivation likely plays in the use of m-
learning. In this study the attitudes of both
faculty and student are examined mid-pandemic
and compared to a previous study on attitudes
pre-pandemic (Bhatnagar, 2019).
2. LITERATURE REVIEW
In the literature several key themes are evident
regarding the intersection of the pandemic and

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 39
https://isedj.org/; https://iscap.info
the evolution of m-learning. This section
discusses those key works, the definitions used in
the context of the study, and theories that have
previously been used to determine attitudes. The
literature points to the validity of the approach
and the importance.
The pandemic shaped key trends on usage of the
Internet. Though mobile broadband usage was
originally expected to peak at 85 percent in 2020,
instead now 95 percent has access to a mobile
broadband network ("Measuring Digital
Development Facts and Figures 2021," 2021). In
spite of this coverage, blind spots persist in rural
areas. In developing countries, the cost of
connecting to mobile broadband remains high,
which restricts access.
M-learning mainly involves the use of mobile
devices and wireless technologies (Pereira &
Rodrigues, 2013) for training, learning, and
teaching purposes (Sarrab, Elgamel, & Aldabbas,
2012) and this is the definition that was used in
the context of this research study. Eteokleous and
Ktoridou (2009) referred to m-learning as a
successor of e-learning. They defined e-learning
as learning that takes place with the use of digital
electronic tools and media. The relationship
between these similar concepts is diagrammed by
Pereira & Rodriguez (2013) and shown in Figure
1.
E-learning moved from being part of the informal
education system to mainstream in learning
delivery ("78 Essential LMS and eLearning
Software Statistics: 2022 Data Analysis & Market
Share," 2022). Widespread acceptance of online
learning is expected to continue post-pandemic.
Cloud-based Learning Management System
(LMS) have enabled the rapid adoption of the
technology. The millennial population in the
workforce is also a driver in the increased use of
m-learning tools.
Some studies have started tracking the
pandemic’s impact on m-learning. In the study of
m-learning for medical education, the importance
of connecting stakeholders (both students and
faculty) and using meaningful interaction with m-
learning was exposed (Kalantrion et al., 2022).
A study of online learning students in Macao
suggests that learning motivation, even in the
case of forced adoption of online, is key to
success (Zhang, Lam, & Su, 2021). A study of m-
learning in the less developed country of Libya
points out the importance of good Internet
connectivity to acceptance even during the forced
adoption caused by the pandemic (Maatuk,
Elberkawi, Aljawarneh, Rashaideh, & Alharbi,
2022).
Though the steps for making radical changes in
organizations have been previously studied
(Cameron & Green, 2019), most organizations did
not have the option of controlled change during
the pandemic. The typical mitigating actions that
would have cushioned the migration to m-
learning such as leading communications,
satisfying needs for emotional security, etc.
(Weiss & Li, 2020) were abbreviated at best.
Furthermore, the assault of change was felt not
just on learning, but in all aspects of existence.
Various theories have been used to explore
attitudes and experiences related to m-learning.
The Technology Acceptance Model (TAM) is
frequently used in industry and in university
settings (Buabeng-Andoh, 2021). The m-learning
paradigm has even inspired the Mobile
Technology Acceptance Model (MTAM) which adds
personal innovativeness and usefulness as
constructs driving adoption (Yuan, Tan, Ooi, &
Lim, 2021). In a study focused on pedagogy and
motivation, a combination of Bloom’s taxonomy
and Malone and Lepper’s Taxonomy of Intrinsic
Motivations for Learning was used as the study
framework (Troussas, Krouska, & Sgouropoulou,
2022).
Similar to Bhatnagar (2019), perceived
usefulness and perceived playfulness has been
Figure 1: Illustration of the evolution
of learning models (Pereira &
Rodrigues, 2013)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 40
https://isedj.org/; https://iscap.info
used to explore student acceptance and rejection
of the mobile learning apps (Al-Bashayreh,
Almajali, Altamimi, Masa’deh, & Al-Okaily, 2022).
This study was created very early in the
pandemic. It was noted in future directions in Al-
Bashayreh et al. (2022) that though pre-
pandemic conditions validated the relationships
between playfulness and intent to use, the
pandemic created an atypical situation where
acceptance may have been forced on students.
3. THEORY
As seen in Al-Bashayreh et al. (2022), the
influence of both intrinsic and extrinsic motivation
factors on mobile information systems use
(MISU) was tested. Intrinsic motivation factors
assessed included perceived enjoyment (PE) and
perceived playfulness (PP). One extrinsic
motivator factor was assessed, perceived
usefulness (PU). Additionally, the influence of
personal innovativeness (PI) on PU, PE, and PP
was also assessed.
The central research question that emerged from
the current state of m-learning research was how
to determine effective use of mobile devices in
the context of mobile information system
applications such as m-learning. Exploring how to
integrate m-learning effectively (Crow, Santos,
LeBaron, McFadden, & Osborne, 2010; Lam, Yau,
& Cheung, 2010) is an important issue that lacks
understanding (Eteokleous & Ktoridou, 2009) and
is a major barrier for its use. It is not enough to
look only at how mobile devices can be
integrated.
Previously Hwang (2014) looked at personal
innovativeness as it related to usage of Enterprise
Resource Planning (ERP) systems. The factors of
PU, PE, and PP were proposed to predict eventual
system usage. This model was adapted as shown
in Figure 2 to predict Mobile Information Systems
Usage (MISU) based on PI, PU, PE, and PP. This
lead to the first research question.
RQ1: What are the motivating factors driving m-
learning use?
The goal was to examine which if any of the
motivating factors of PU, PE, and PP were
impacting MISU. Therefore, the following
hypotheses were tested using the proposed
theoretical model in Figure 2 to answer RQ1.
H
0
1: PU, PE, and PP positively and significantly
influence MISU.
H1a: PI will positively and significantly influence
PU.
H1b: PI will positively and significantly influence
PE.
H1c: PI will positively and significantly influence
PP.
Figure 2: Proposed Theoretical Model adopted from Hwang (2014)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 41
https://isedj.org/; https://iscap.info
H2a: PU will positively and significantly influence
MISU.
H2b: PE will positively and significantly influence
MISU.
H2c: PP will positively and significantly influence
MISU.
The second research question looks at what is
being included in MISU. Particularly in the mid-
pandemic timeframe, the range of activities
included in m-learning expanded drastically, as
did the participating population in comparison to
pre-pandemic. This reality incited the second
question.
RQ2: How is m-learning being used for teaching,
learning, and training?
RQ2 was answered via four questions in the
survey instrument. These can be seen in
Appendix A & B.
The hypotheses, graphically displayed in Figure 3,
were tested using the theoretical model (Figure
2) to answer both research questions via the
survey instrument. PI will positively and
significantly influence PU, PE, and PP (H1a, H1b,
H1c) and PU, PE, and PP will positively and
significantly influence MISU (H2a, H2b, and H2c).
4. METHODOLOGY AND PROCEDURE
Institutional Review Board approval was received
at the primary investigator’s institution prior to
commencing the study. An online survey was
created using Qualtrics and analyzed using
Structural Equation Modeling. The questions
replicated those used in a study of pre-pandemic
attitudes towards mobile learning (Bhatnagar,
2019). The survey also contained questions to
help understand how m-learning is being used for
teaching and learning. For details, please see
Appendix A (Faculty Survey Instrument) and
Appendix B (Student Survey Instrument).
Participants were contacted via email and
requested to participate in the study. Whereas
the previous study focused only on faculty
teaching in the disciplines of computer science,
information systems, and business at 60
institutions of higher education (both public and
private) who are members of the Association of
American Universities (AAU) in the United States,
this study was expanded to also include students.
Faculty and students at a regional campus of an
R1 university in western Pennsylvania along with
international students at a European university
took the survey. This provides a sample set with
wider cultural representation.
The initial email was sent to a total of 959
undergraduate students, 16 graduate students
and 186 faculty. A reminder email was sent after
one week to 979 undergraduate students and 187
faculty. Additional students had been added to
the shared email list in the time since the initial
email, so more students were contacted in the
reminder. The response rates for both faculty and
students were significantly low at 9% and 4%
respectively.
The data was first cleaned by removing blank
records, and incomplete responses. The data was
then coded. Microsoft Excel, SPSS and SmartPLS
were used for the data analysis.
In addition to the questions of the original survey
(Bhatnagar, 2019), a measurement of usability
was also taken using the System Usability Scale
(SUS) metric. The importance of student
satisfaction during the pandemic forced adoption
(Uthman & Ahmed, 2022) seemed to be a critical
factor. Usability measures like SUS indicate how
users feel about the experience of using the
system. Though previous studies of the effect of
Computer Anxiety (CA) had not shown a direct
relationship between CA and the intention to use
(Ball & Levy, 2008), studies during the pandemic
have shown otherwise (Alsubaie, Alzarah, &
Alhemly, 2022). The amount of change induces
technostress which means more attention needs
to be paid to the student and faculty experience.
The reliability and validity of SUS has been
documented by 20 years of SUS Scores (Sauro,
Figure 3: Conceptual Map of the
Research Model

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 42
https://isedj.org/; https://iscap.info
2011). Reliability refers to the consistent
response to the items. SUS detects differences in
smaller sample sizes (as few as two users) and
generates reliable results. Validity refers to
whether an instrument measures the target,
which for SUS is perceived usability. SUS has
been shown to effectively distinguish between
unusable and usable systems and correlates
highly with other questionnaire-based
measurements of usability. These characteristics
combine to make SUS an improvement to
commercial alternatives and home-grown
questionnaires (Sauro, 2011). The SUS provides
a comprehensive measure in addition to the
dimensionality measures of the original
instrument.
The discussion of key results is divided into two
sections. The first section provides a comparison
of the results between the pre-pandemic and mid-
pandemic findings. The second section looks at
the student data results.
5. COMPARISON PRE/MID PANDEMIC
RESULTS FOR FACULTY
SPSS was used to perform pre-analysis data
screening. Outliers, or extreme cases, in the data
were evaluated for all datasets using both the
univariate and multivariate techniques. Since the
data was coded on a 7-point Likert scale, a visual
inspection of the data showed no univariate
outliers. With 24 items, the degrees of freedom is
24 and the critical value for chi-square at p<.001
equals 51.179. For the current study, the analysis
called for the elimination of one case, but it was
not removed. In the pre-pandemic study six cases
had to be removed since the Mahalanobis
distance was greater than 51.179.
Structural model analysis was done in two parts.
The measurement model focuses on internal
consistency reliability, convergent validity, and
discriminant validity. The structural model is
assessed by evaluating collinearity, the
significance of path coefficients, the level of R
2
values, the f
2
effect size, the predictive relevance
(Q
2
), and the q
2
effect size (Hair Jr, Hult, Ringle,
& Sarstedt, 2013).
Measurement Model
Internal consistency reliability is measured by
evaluating composite reliability and Cronbach’s
alpha. Composite reliability ranges between zero
and one. The higher the number, the higher the
composite reliability. Cronbach’s alpha greater
than 0.8 are good. The model showed strong
internal consistency reliability for both the pre-
pandemic and mid-pandemic studies.
The two most common measures of construct
validity are convergent and discriminant validity.
Any reflective indicator whose outer loading is
below 0.4 should be removed. However,
indicators with outer loadings between 0.4 and
0.7 should be further analyzed by looking at the
impact on composite reliability and average
variance extracted (AVE) before any elimination
takes place (Hair Jr et al., 2013).
In the pre-pandemic study, MISU7 had an outer
loading of -0.358, in this study it is 0.044. Since
Table 1: Comparative Analysis of Results for Faculty

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 43
https://isedj.org/; https://iscap.info
it is below 0.4, it should be removed. PP1 and PP2
have outer loadings between 0.4-0.7, 0.681 and
0.697 respectively (in the previous study with
0.641 and 0.495 respectively). These were
further examined by looking at the impact on
composite reliability and average variance
extracted (AVE) before their elimination. As was
the case in the previous study, composite
reliability, Cronbach’s alpha, and AVE are greatly
improved by removing MISU7, PP1, and PP2.
These three indicators were removed prior to
completing the remainder of the analysis. The
indicator reliability is the squared value of an
indicator’s outer loading.
Discriminant validity is assessed by examining
the indicator cross loadings and the Fornell-
Larcker criterion. In both studies these were met
without any issues.
Structural Model
The structural model is assessed by evaluating
collinearity, the significance of path coefficients,
the level of R
2
values, the f
2
effect size, the
predictive relevance (Q
2
), and the q
2
effect size
(Hair et al., 2013). These are discussed next.
SPSS was used to assess collinearity. Collinearity
involves examining tolerance levels and the
variance inflation factor (VIF). Tolerance levels
below 0.2 and VIF above 5.0 are indicators of
collinearity. In both studies the results indicate no
collinearity issues.
Structural model path coefficients should be
between -1 and +1. Coefficients that are close to
+1 represent a strong positive relationship, -1 a
strong negative relationship, and close to zero a
weak or nonsignificant relationship (Hair et al.,
2013). Since the hypotheses for the study are
unidirectional, this implies a one-tailed test. In
the pre-pandemic study, two of the paths were
not significant, from PE to MISU (rejecting H2b)
and from PP to MISU (rejecting H2c). In this study
besides these two, the path from PP to MISU is
also not significant (rejecting H2a).
The coefficient of determination, R
2
,
value ranges
from 0 to 1 and there is no agreed upon value for
an acceptable R
2
value (Hair et al., 2013).
However, Hair et al. stated that values of 0.75
(substantial), 0.50 (moderate), and 0.25 (weak)
can be used as a rule of thumb. Based on the
results, MISU, PE, PI, and PP had weak predictive
accuracy in the pre-pandemic study. In this
study, PI did not appear in the results and the
remaining constructs have a moderate predictive
accuracy.
According to Hair et al. (2013), effect size (f
2
)
values of 0.02 (small), 0.15 (medium), and 0.35
(large) are the effect sizes that should be used to
evaluate the structural model. In the previous
study, PI had a large effect on PE, a medium
effect on PP. and a small effect on PU and PU had
a small effect on MISU. In this study, PI has a
large effect on PU, PE, and PP whereas PU and PE
have medium effects on MISU and PP has a small
effect on MISU.
Blindfolding is a method used to calculate
predictive relevance (Q
2
). Q
2
indicates the
model’s predictive relevance (Hair Jr et al.,
2013). Assessment of Q
2
uses the same values
for small, medium, and large as f
2
. While the pre-
pandemic study showed the model to have some
predictive relevance, even if minimal, in the
current study the model has a stronger predictive
relevance.
Just as f
2
effect size is used to assess R
2
values,
relative impact of predictive relevance can be
compared by means of the measure to the q
2
effect size (Hair Jr et al., 2013). The equation to
calculate the q
2
effect is seen below.
(Q
2
included – Q
2
excluded) / (1-Q
2
included)
The values of 0.02, 0.15, and 0.35 show small,
medium, or large predictive relevance. MISU is
the endogenous variable. By removing each of
the latent variables (PE, PU, and PI) one at a time,
and calculating the predictive relevance,
determines the effect size of each latent variable
on the endogenous variable. In the previous
study it was determined that all predictor
variables had a very small effect size. In this
study, PE and PU have a medium effect size while
PP has a small effect size. Table 1 summarizes the
Figure 4: Faculty age range

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 44
https://isedj.org/; https://iscap.info
findings of the mid- and pre-pandemic data
results for faculty.
Faculty Demographics
In the current study, analysis of the faculty
demographics showed that the survey was
completed primarily by females (56%) in the age
ranges shown in Figure 4. Overwhelmingly 81%
have earned doctorate degrees and teach in
disciplines other than Information Systems,
Business, and Computer Science. The disciplines
in which participants obtained their higher degree
was wide ranging. All participants (100%) teach
at the undergraduate level. It was interesting to
find that 31% of them teach on-campus (i.e. in-
person, face-to-face) and hybrid in spite of the
pandemic.
The average number of years of teaching
experience is 22 years and the average number
of years in higher education is 20 years. A
majority are employed full-time (75%) and teach
at a public university (94%). The average years
of teaching on-campus are 19, online 5, and
hybrid 3. Most are not on tenure track (62%).
Pre-Pandemic M-Learning Uses
The uses of m-learning (which address RQ2)
showed that 18% of the participants using m-
learning (n=87) used four of the five options
provided: in-class and out-of-class activities,
online and hybrid course. Around 8% used one or
more combinations of the options provided. The
types of activities being used for m-learning in
teaching were wide ranging. See Appendix C for
the types of activities surveyed.
Of the 87 participants who identified themselves
as users of m-learning, three (3%) stated that
they had been using m-learning for less than one
year, 55 (63%) started using m-learning between
1 to 6 years ago, seven (8%) between 7 to 10
years, and 22 (25%) had started using it over ten
years ago. Seventy-six (87%) use it anywhere
from several times a day to 3-5 days a week. The
remaining 11 participants (or 12%) use it less
frequently. Sixty-three (72%) of the 87
participants stated that they felt moderately or
very comfortable using m-learning.
Teaching resources provided on a mobile device
resulted in 61 combinations of choices. The top
three choices accounted for 17% of the resources
used. These include using a combination of
lecture PPT slides, audio, and video recordings,
print content, eBooks, hyperlinks to course-
related reference material, and Blackboard. Some
participants also provided information on other
resources provided to students on a mobile
device. The most commonly listed system was
Canvas.
In general, most participants (86%) expressed a
level of satisfaction in using m-learning that
ranged between somewhat to mostly satisfied.
Hardware used for m-learning primarily includes
generic laptops, phones, video cameras,
computers, and e-readers. Next would be all the
Apple products (iPhone, iPad, mac, MacBook).
The predominant software used is Canvas. Others
used are wide-ranging (Bhatnagar, 2019).
Mid-Pandemic M-Learning Uses
Faculty are currently using m-learning for all of
the following options (in various types of
combinations): in-class and out-of-class
activities, online course, hybrid course, as well as
for professional development/training. All 16
participants started using m-learning over a year
ago, eleven (70%) have been using it between 1
to 6 years, two (12%) have been using it between
7 to 10 years, and the remaining three (18%)
have been using it over 10 years. Sixty-two
percent use it anywhere from several times a day
to about once a day. Twenty-five percent use it
3-5 days a week, twelve percent use it 1-2 days
a week, twelve percent use it every few weeks or
less often, and only six percent has never used it.
Two new questions were added to the survey. The
first asked if participants were given a choice
other than mobile learning during the pandemic.
Thirty-seven percent said yes, and sixty-three
percent said no.
Of those that stated they were not given a choice,
all participants stated that they did not choose to
not teach to avoid mandatory mobile learning.
Almost seventy percent stated they are
moderately or very comfortable in using m-
learning. Teaching resources provided on a
mobile device resulted in 14 combinations from
the choices that were provided. Some of these
choices included lecture PPT slides, audio, and
video recordings, among others. A majority
(87.5%) expressed a level of satisfaction ranging
from neither satisfied nor dissatisfied to
somewhat satisfied. Participants were asked to
identify how frequently they engaged in various
types of activities using their mobile devices to
support teaching. See Appendix C for a
breakdown of the responses. In a follow-up
question most participants (68%) said they did
not engage in any other activities using mobile
devices to support teaching.
Hardware used for m-learning primarily includes
phones and laptops. Canvas is the learning
management system used at the regional campus

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 45
https://isedj.org/; https://iscap.info
where the survey was administered and chosen
by majority of the participants. There were a
myriad of other software programs identified,
some discipline specific.
6. MID-PANDEMIC STUDENT RESULTS
As discussed earlier, students were added to the
study for the mid-pandemic study. In the
conditions of the mid-pandemic, it was felt
student results, though not part of the previous
study, were also relevant. This section analyzes
the student data.
Measurement Model
There were no outlier cases with a value greater
than 51.179 that had to be eliminated. The model
showed strong internal consistency reliability for
all constructs except PP. Convergent validity
analysis showed the outer loadings for PP1
between 0.4 and 0.7 and below 0.4 for MISU7 and
PP2. As such composite reliability, Cronbach’s
alpha, and AVE greatly improve by removing
MISU7, PP1, and PP2. These indicators were
removed before proceeding the remainder of the
analysis. Indicator cross loadings and the Fornell-
Larcker criterion were met without any issues
indicating no issues with discriminant validity.
Structural Model
Analysis of the constructs showed collinearity
issues with PP in terms of tolerance and VIF.
Based on the structural model and path
coefficients, two of the paths were not significant,
from PI to PE (rejecting H1b) and from PP to MISU
(rejecting H2c). The coefficient of determination
(R
2
) values for PE, PI, and PP indicate weak
predictive accuracy. In terms of effect size (f
2
),
PU and PE have a large effect on MISU, PI has a
medium effect on PE, PU, and PP, and PP has a
small effect on MISU. Blindfolding and predictive
relevance (Q
2
) showed that the model does have
predictive relevance. Effect size (q
2
) indicates
that all predictor variables have a medium to
large effect size.
Student Demographics
Analysis of the student demographics questions
shows that the average age of the participants is
20 years old. The survey was completed by more
females (48%) than males (46%). A majority of
the students were undergraduates (78%) and
19% were graduate students. The graduate
students were primarily pursuing business
degrees while the undergraduate students
represented a variety of disciplines such as
business, management, biological sciences,
information technology/cybersecurity, nursing,
psychology, among others. Some of the
disciplines were listed as double majors.
7. DISCUSSION
Several important conclusions emerge from the
analysis. The results of the study related to the
hypotheses are shown in Table 2.
Pre/Mid Pandemic (Faculty)
In both the pre-pandemic and the current study,
PI did positively and significantly influence PU, PE,
and PP. This led to accepting H1a, H1b, and H1c.
Hwang’s (2014) research had explored testing
the impact of personal innovativeness of IT (PIIT)
on the intrinsic motivation factors perceived
enjoyment (PE) and perceived ease of use (PEOU)
and the extrinsic motivation factor of perceived
usefulness (PU) as it related to the use of ERP
systems. Hwang arrived at similar conclusions
with PIIT influencing PE, PEOU, and PU. In the
context of both studies, the fact that PI positively
and significantly influences PE, PU, and PP implies
that the participants are willing to try using new
technologies, such as mobile information
systems, because they find these systems to be
useful, enjoyable, and like interacting with these.
Also in the pre-pandemic study, PU was found to
positively influence MISU, but this is not the case
for the mid-pandemic study. Prior to the
pandemic, this implied that participants are using
mobile information systems (m-learning) because
they find m-learning to be useful for teaching and
student learning. Even earlier studies of the
impact of PU on IS continuance intention using
Blackberry hardware showed PU positively
impacted IS use (Chen, Meservy, & Gillenson,
2012).
For the mid-pandemic, in spite of perceived
usefulness, the participants did not find that a
motivator for MISU.
Third, in the previous study, PE and PP did not
influence MISU which meant that using mobile
Table 2: Summary of Hypotheses
(Faculty)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 46
https://isedj.org/; https://iscap.info
information systems for m-learning was not
perceived to be enjoyable or interesting to use or
that enjoyment and playfulness were not the
reasons that would influence using mobile
information systems, such as m-learning. This is
also true for the current study.
Fourth, based on R
2
and Q
2
values, the model has
a weak predictive accuracy and minimal
predictive relevance, whereas in the current
study, the model shows moderate predictive
accuracy and a strong predictive relevance.
Fifth, in the pre-pandemic study, the f
2
of PE and
PP has no effect on MISU, which also confirmed
the rejection of H2b and H2c while the other
effect sizes confirm accepting H1a, H1b, H1c, and
H2a. In the current study, there were no f
2
values
which had no effect on MISU even though the
structural paths indicate that H2a, H2b and H2c
should be rejected.
Lastly, in the previous study the q
2
effect size
showed little to no significance for PE, PU, and PP
while in the current study the significance is small
for PP and medium for PE and PU.
Mid-Pandemic (Student)
As seen in Table 3, the student results matched
the faculty response for H1a, H1c and H2c. The
effect of PI on PE was rejected by the students
(H1b). Unlike the faculty in the mid-pandemic
result, the effect of PU and PE on MISU were
accepted.
Table 3: Summary of Hypotheses (Student)
The students do feel enjoyment will encourage
MISU. But they do not feel that playfulness will
encourage MISU. Considering that these results
were obtained in a time period where adoption of
MISU was mandatory due to the pandemic,
students may be expressing a frustration with the
lack of options.
SUS
Examining the SUS data from both the faculty and
student revealed the perception of a lack of
usability in the m-learning applications. Analysis
of the SUS data typically yields a letter grade of
A-F. The participants rated the usability of m-
learning at a solid D, or barely acceptable.
This finding is interesting, in light of the contrast
between student and faculty results for perceived
enjoyment. Student results did support that PE
positively influenced MISU. Faculty results did
not. But neither rated the usability of m-learning
favorably. Once again, this points to the
technostress induced by the intense and rapid
implementation due to COVID-19 (Uthman &
Ahmed, 2022). The stress on both faculty and
students did not make them feel m-learning
systems were usable.
In addition, the 81% of the faculty participants
were not teaching the more technological
subjects of Information Systems, Computer
Science, or Business. The low usability score may
also be affected by lesser expertise in technology.
8. CONTRIBUTIONS, LIMITATIONS, AND
FUTURE RESEARCH
Contributions
The results achieved from the study are valuable
and provide significant contributions to the body
of knowledge. The research helped 1) identity
motivation factors driving the use of mobile
information systems for m-learning, 2)
understand how m-learning is being used for
teaching, learning, and training. The research
extends prior research on m-learning which has
been deficient in understanding faculty use of m-
learning.
No prior research studies were found that looked
at motivation factors for the use of m-learning
and were limited on understanding faculty use
with most research focused on student use.
Research on information systems use is ample
but research focusing on mobile information
systems use is limited or nonexistent. Finally,
research on motivation to use m-learning during
forced adoption due to a global health crisis is
non-existent. This is the unique contribution of
this research to the fields of Human Computer
Interaction/User Experience (HCI/UX),
Information Systems, and M-learning.
Limitations
Limitations of both the pre-pandemic and mid-
pandemic studies include the limited participants
who were contacted to participate in the study,
affecting the generalizability of the studies. The
mid-pandemic study had a specific window of
time to gather results before conditions shifted
again. Additionally, the low response rate and
self-reporting by participants completing an
online survey may have introduced bias in the
Hypotheses
Construct
Result
H1a
PI → PU
Accept
H1b
PI → PE
Reject
H1c
PI → PP
Accept
H2a
PU → MISU
Accept
H2b
PE → MISU
Accept
H2c
PP → MISU
Reject

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 47
https://isedj.org/; https://iscap.info
responses received.
Future Research
Given the limited scope of the study, it is evident
that more research is needed. It should also be
expanded to include more institutions of higher
education and additional disciplines. Non-
response rate and the generalizability of the study
must also be accounted for. Grounding the study
in other information systems theories that may
better explain use or non-use is also suggested.
This would allow investigating other factors
beyond PI, PU, PE, and PP, such as resistance to
use. Finally, as suggested by Ball and Levy
(2008), research on methods to encourage
instructors in the use of emerging technology
would benefit both the researchers and
practitioners. Such research could address the
technostress (Uthman & Ahmed, 2022)
experienced by both students and instructors.
It is hoped the results of this study may be
compared to future research that repeats these
questions in a post-pandemic world. In the future
study the constructs PP1, PP2, and MISU7 (as
seen in Figure 1) should not be included because
composite reliability, Cronbach’s alpha, and AVE
are improved when they are removed. Further
comparison of the data to a reality without forced
adoption may reveal insights on motivations. The
forced adoption may be a key factor in motivation
and user satisfaction.
9. CONCLUSION
The data for motivating factors shows some
differences between faculty and student attitudes
towards m-learning. Some shift in perception is
also shown based on pre-pandemic to mid-
pandemic. As the situations surrounding the
implementation of m-learning continue to shift, it
will be of interest to see how this influences the
attitudes of faculty and student. Information
System (IS) educators should be aware of the
negative attitudes towards perceived usefulness
and perceived usability of m-learning systems.
10. ACKNOWLEDGEMENTS
The portion of this research that took place at a
European university was supported by the U.S
scholar program through the Fulbright
commission. The authors would also like to thank
the participants for providing data in a timely
manner to allow analysis at this unique point in
m-learning usage.
11. REFERENCES
78 Essential LMS and eLearning Software
Statistics: 2022 Data Analysis & Market
Share. (2022). Retrieved from
https://financesonline.com/lms-and-
elearning-software-statistics/
Al-Bashayreh, M., Almajali, D., Altamimi, A.,
Masa’deh, R. e., & Al-Okaily, M. (2022). An
empirical investigation of reasons influencing
student acceptance and rejection of mobile
learning apps usage. Sustainability, 14(7),
4325.
Alsubaie, M. A., Alzarah, L. N., & Alhemly, F. A.
(2022). Faculty Members’ Attitudes and
Practices: How They Responded to Forced
Adoption of Distance Education? SAGE Open,
12(3), 21582440221108165.
doi:10.1177/21582440221108165
Ball, D. M., & Levy, Y. (2008). Emerging
educational technology: Assessing the factors
that influence instructors’ acceptance in
information systems and other classrooms.
Journal of Information Systems Education,
19(4), 431.
Bhatnagar, N. (2019). Motivation Factors for
Using Mobile Information Systems in M-
Learning. Nova Southeastern University.
Buabeng-Andoh, C. (2021). Exploring University
students’ intention to use mobile learning: A
research model approach. Education and
Information Technologies, 26(1), 241–256.
doi:10.1007/s10639-020-10267-4
Cameron, E., & Green, M. (2019). Making sense
of change management: A complete guide to
the models, tools and techniques of
organizational change: Kogan Page
Publishers.
Chen, L., Meservy, T. O., & Gillenson, M. (2012).
Understanding information systems
continuance for information-oriented mobile
applications. Communications of the
Association for Information Systems, 30(1),
9.
Crow, R., Santos, L. M., LeBaron, J., McFadden,
A. T., & Osborne, C. F. (2010). Switching
gears: moving from e-learning to m-learning.
MERLOT Journal of Online Learning and
Teaching, 6(1), 268-278.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 48
https://isedj.org/; https://iscap.info
Eteokleous, N., & Ktoridou, D. (2009).
Investigating mobile devices integration in
higher education in Cyprus: Faculty
perspectives. International Journal of
Interactive Mobile Technologies, 3(1).
Hair Jr, J. F., Hult, G. T. M., Ringle, C. M., &
Sarstedt, M. (2013). A primer on partial least
squares structural equation modeling (PLS-
SEM): Sage publications.
Hwang, Y. (2014). User experience and personal
innovativeness: An empirical study on the
enterprise resource planning systems.
Computers in Human Behavior, 34, 227-234.
doi:10.1016/j.chb.2014.02.002
Kalantrion, M., Sadoughi, M.-M., Ahmady, S.,
Kallestrup, P., Katibeh, M., & Khajeali, N.
(2022). Introducing a mobile learning model
in medical education during COVID-19; a
critical review. Journal of Advances in Medical
Education & Professionalism, 10(3), 145-155.
Lam, J., Yau, J., & Cheung, S. K. (2010). A review
of mobile learning in the mobile age. Paper
presented at the International Conference on
Hybrid Learning.
Maatuk, A. M., Elberkawi, E. K., Aljawarneh, S.,
Rashaideh, H., & Alharbi, H. (2022). The
COVID-19 pandemic and E-learning:
challenges and opportunities from the
perspective of students and instructors.
Journal of Computing in Higher Education,
34(1), 21-38.
Measuring Digital Development Facts and Figures
2021. (2021). Retrieved from
https://www.itu.int/en/ITU-D/Statistics/
Documents/facts/FactsFigures2021.pdf
Pereira, O. R., & Rodrigues, J. J. (2013). Survey
and analysis of current mobile learning
applications and technologies. ACM
Computing Surveys (CSUR), 46(2), 1-35.
Sarrab, M., Elgamel, L., & Aldabbas, H. (2012).
Mobile learning (m-learning) and educational
environments. International Journal of
Distributed & Parallel Systems, 3(4), 31-38.
doi:10.5121/ijdps.2012.3404
Sauro, J. (2011). Measuring usability with the
system usability scale (SUS).
Troussas, C., Krouska, A., & Sgouropoulou, C.
(2022). Enriching Mobile Learning Software
with Interactive Activities and Motivational
Feedback for Advancing Users’ High-
Level Cognitive Skills. Computers, 11(2), 18.
Uthman, A., & Ahmed, A. (2022). Students’
Perceptions of the Actual Use of Mobile
Learning during COVID-19 Pandemic in
Higher Education. Sustainability (Basel,
Switzerland), 14(3), 1125.
doi:10.3390/su14031125
Weiss, P. G., & Li, S.-T. T. (2020). Leading
Change to Address the Needs and Well-Being
of Trainees During the COVID-19 Pandemic.
Academic Pediatrics, 20(6), 735-741.
doi:https://doi.org/10.1016/j.acap.2020.06.
001
Yuan, Y.-P., Tan, G. W.-H., Ooi, K.-B., & Lim, W.-
L. (2021). Can COVID-19 pandemic influence
experience response in mobile learning?
Telematics and Informatics, 64, 101676.
Zhang, H., Lam, J. F. I., & Su, S. (2021). A
Qualitative Research on the Online Learning
Experiences of College Students in Macao
during the Pandemic. Paper presented at the
2021 5th International Conference on
Education and E-Learning, Virtual Event,
Japan. https://dl.acm.org/doi/10.1145
/3502434.3502470

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 49
https://isedj.org/; https://iscap.info
APPENDIX A
Faculty Survey Instrument
1 Which of the following best describes YOUR use of m-learning at your current institution? Please
check all that apply.
For in-class activities
For out-of-class activities
For an online course
For a hybrid course (combination of in-class
and online)
For professional development/training
Scale for items 2 through 6:
[1] strongly disagree, [2] disagree, [3] strongly disagree, [4] neither agree or disagree, [5] slightly
agree, [6] agree, [7] strongly agree
2 Personal Innovativeness (PI) - "willingness of an individual to try out any new information
technology." (Agarwal & Prasad, 1998, p. 260)
PI1. If I hear about new information technology, I will look for ways to experiment with it.
PI2. Among my faculty peers, I am usually the first to try out new information technologies.
PI3. In general, I am not hesitant to try out new information technologies.
PI4. I like to experiment with new information technologies.
3 Perceived Usefulness (PU) - "degree to which a person believes that using a particular system would
enhance his or her job performance." (Davis, 1989, p. 320)
PU1. Using m-learning makes it easier to teach.
PU2. Using m-learning enhances my teaching effectiveness.
PU3. Using m-learning gives me greater control over teaching.
PU4. I find m-learning to be useful in my teaching.
4 Perceived Enjoyment (PE) - "extent to which the activity of using the computer is perceived to be
enjoyable in it's own right, apart from any performance consequences, that may be anticipated."
(Davis et al., 1992, p. 1113)
PE1. Using m-learning is fun.
PE2. Using m-learning is enjoyable.
PE3. Using m-learning is very entertaining (pleasant).
PE4. Using m-learning is interesting.
5 Perceived Playfulness (PP) - "the extent to which the individual finds the interaction intrinsically
enjoyable or interesting." (Moon & Kim, 2001, p. 219)
PP1. When using m-learning, I will not realize the time elapsed.
PP2. When using m-learning, I will forget the work I must do.
PP3. Using m-learning will give enjoyment to me for my teaching.
PP4. Using m-learning will stimulate my curiosity.
PP5. Using m-learning will lead to my exploration.
6 Mobile Information System Use (MISU) - involves the use of mobile devices to use an information
system to "...carry out tasks and activities on the job for which the information system is designed to
support" (Sun & Teng, 2012). Examples would include using learning management systems such as
Blackboard and Banner.
MISU1. I use mobile information systems on a regular basis.
MISU2. I will continue to use mobile information system in the future.
MISU3. I intend to continue using mobile information systems.
MISU4. I want to continue using mobile information systems rather than discontinue.
MISU5. I predict I will continue using mobile information systems.
MISU6. I plan to continue using mobile information systems.
MISU7. I will stop using mobile information systems in the future.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 50
https://isedj.org/; https://iscap.info
7 Rate each of the following statements:
[1] strongly disagree, [2] disagree, [3] neither agree or disagree, [4] agree, [5] strongly agree
I think that I would like to use mobile learning frequently.
I found mobile learning to be simple.
I thought mobile learning was easy to use.
I think that I could use mobile learning without the support of a technical person.
I found the various functions in mobile learning were well integrated.
I thought there was a lot of consistency in mobile learning.
I would image that most people would learn to use mobile learning very quickly.
I found mobile learning very intuitive.
I felt very confident using mobile learning.
I could use mobile learning without having to learn anything new.
8 How long ago did YOU start using m-learning?
Less than 1 year
1-2 years
3-4 years
5-6 years
7-8 years
9-10 years
More than 10 years
9 How often do YOU use m-learning? Please check all that apply.
Several times a day
About once a day)
3-5 days a week
1-2 days a week
Every few weeks
Less often
Never
10 Were you given a choice other than mobile learning during the pandemic?
Yes
No
11 Did you choose to not teach to avoid mandatory mobile learning?
Yes
No
12 What is your level of comfort in using m-learning?
Very uncomfortable
Moderately uncomfortable
Slightly uncomfortable
Neutral
Slightly comfortable
Moderately comfortable
Very comfortable
13 Which of the following teaching resources do YOU provide on a mobile device? Select all that apply.
Lecture PPT slides
Audio recordings (e.g. recordings of lectures, school information)
Videos (e.g. course-related, recordings of lectures, school information)
Print content
Ebooks
Flashcards and other interactive educational games
Hyperlinks to course-related reference material
Blackboard
Other: please specify
14 Rate your level of satisfaction with the use of m-learning.
Completely dissatisfied
Mostly dissatisfied
Somewhat dissatisfied
Neither satisfied or dissatisfied
Somewhat satisfied
Mostly satisfied

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 51
https://isedj.org/; https://iscap.info
Completely satisfied
15 How frequently do you engage in the following activities using your mobile device(s) to support
teaching?
[1] Never, [2] Rarely, [3] Occasionally, [4] Sometimes, [5] Frequently, [6] Usually, [7] Always
Emailing students
Emailing colleagues
Texting students
Texting colleagues
Posting grades
Posting to discussion boards
Accessing course site
Accessing library resources
Accessing social networking
Ordering textbooks
Searching the internet
Providing tutoring services
Preparing lessons
Conducting seminars
Collecting content for coursework
Reading ebooks
Taking pictures or making videos to include in
your courses
As a follow-up to the previous question, do you engage in any other activities using your mobile
device(s) to support teaching?
Yes, please specify:
No
16 What technologies do you use for m-learning (hardware, software)?
17 To which gender identify do you most identify?
Male
Female
Transgender female
Transgender male
Gender variant/non-conforming
Not listed
Prefer not to answer
18 Please indicate your age group
20-29
30-39
40-49
50-59
60-69
70-79
80 and over
19 Your number of years of teaching experience:
20 Your number of years in higher education:
21 Your academic rank
Lecturer
Instructor
Assistant Professor
Associate Professor
Professor
Emeritus
Other: please specify
22 Please indicate highest education level achieved.
Master's
Doctorate
Professional degree: please specify:
Other: please specify
23 Please indicate the discipline in which you obtained your highest degree:

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 52
https://isedj.org/; https://iscap.info
24 Please indicate your program area/discipline in which you are currently teaching:
Information Systems
Business: please specify
Other:
25 What college level are you teaching?
Undergraduate
Graduate
Both undergraduate and graduate
26 Do you teach courses for students? Select all that apply.
On-campus (in-person, face-to-face)
Off-campus (purely online)
Hybrid (on-campus and online)
27 How long have you been teaching on campus? (i.e. in-person, face-to-face) courses?
28 How long have you been teaching online courses?
29 How long have you been teaching hybrid courses?
30 Do you teach full-time or part-time?
Full-time
Part-time
31 Please indicate the type of university you are currently affiliated with.
Public
Private
32 What is your tenure status?
Currently hold tenure at this institution
Currently on tenure-track at this institution
Not on tenure-track at this institution
Tenure is not available at this institution

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 53
https://isedj.org/; https://iscap.info
APPENDIX B
Student Survey Instrument
Scale for items 1 through 5:
[1] strongly disagree, [2] disagree, [3] strongly disagree, [4] neither agree or disagree, [5] slightly
agree, [6] agree, [7] strongly agree
1 Personal Innovativeness (PI) - "willingness of an individual to try out any new information
technology." (Agarwal & Prasad, 1998, p. 260)
PI1. If I hear about new information technology, I will look for ways to experiment with it.
PI2. Among my student peers, I am usually the first to try out new information technologies.
PI3. In general, I am not hesitant to try out new information technologies.
PI4. I like to experiment with new information technologies.
2 Perceived Usefulness (PU) - "degree to which a person believes that using a particular system would
enhance his or her job performance." (Davis, 1989, p. 320)
PU1. Using m-learning makes it easier to learn.
PU2. Using m-learning enhances my learning effectiveness.
PU3. Using m-learning gives me greater control over learning.
PU4. I find m-learning to be useful in my learning.
3 Perceived Enjoyment (PE) - "extent to which the activity of using the computer is perceived to be
enjoyable in it's own right, apart from any performance consequences, that may be anticipated."
(Davis et al., 1992, p. 1113)
PE1. Using m-learning is fun.
PE2. Using m-learning is enjoyable.
PE3. Using m-learning is very entertaining (pleasant).
PE4. Using m-learning is interesting.
4 Perceived Playfulness (PP) - "the extent to which the individual finds the interaction intrinsically
enjoyable or interesting." (Moon & Kim, 2001, p. 219)
PP1. When using m-learning, I will not realize the time elapsed.
PP2. When using m-learning, I will forget the work I must do.
PP3. Using m-learning will give enjoyment to me for my learning.
PP4. Using m-learning will stimulate my curiosity.
PP5. Using m-learning will lead to my exploration.
5 Mobile Information System Use (MUSE) - involves the use of mobile devices to use an information
system to "...carry out tasks and activities on the job for which the information system is designed to
support" (Sun & Teng, 2012). Examples would include using learning management systems such as
Blackboard and Banner.
MISU1. I use mobile information systems on a regular basis.
MISU2. I will continue to use mobile information system in the future.
MISU3. I intend to continue using mobile information systems.
MISU4. I want to continue using mobile information systems rather than discontinue.
MISU5. I predict I will continue using mobile information systems.
MISU6. I plan to continue using mobile information systems.
MISU7. I will stop using mobile information systems in the future.
Scale for question 6:
[1] strongly disagree, [2] disagree, [3] neither agree or disagree, [4] agree, [5] strongly agree

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 54
https://isedj.org/; https://iscap.info
6 Rate each of the following statements:
I think that I would like to use mobile learning frequently.
I found mobile learning to be simple.
I thought mobile learning was easy to use.
I think that I could use mobile learning without the support of a technical person.
I found the various functions in mobile learning were well integrated.
I thought there was a lot of consistency in mobile learning.
I would image that most people would learn to use mobile learning very quickly.
I found mobile learning very intuitive.
I felt very confident using mobile learning.
I could use mobile learning without having to learn anything new.
7 To which gender identity do you most identify?
Male
Female
Transgender female
Transgender male
Gender variant/non-conforming
Not listed
Prefer not to answer
8 I am a (n)
Undergraduate student
Graduate student
If I am a (n) = Undergraduate student
9 What is your level?
Freshman
Sophomore
Junior
Senior
10 What is your age?
11 What is your major?

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 55
https://isedj.org/; https://iscap.info
APPENDIX C
Mid-Pandemic Faculty M-Learning Activities Usage
* See section 5 for a detailed discussion of Appendix C
Activity
Never
Rarely
Occasionally
Sometimes
Frequently
Usually
Always
Email students
1
1
3
1
5
1
4
Email
colleagues
1
1
3
0
6
1
4
Text students
5
4
2
4
0
0
1
Text colleagues
2
4
0
3
6
0
1
Post grades
3
3
2
3
2
0
3
Post to
discussion
board
3
3
3
6
1
0
0
Access course
site
0
4
0
2
7
0
3
Access library
resources
2
2
1
5
3
3
0
Access social
networking
2
2
0
1
7
2
2
Order
textbooks
7
2
2
2
1
1
1
Search internet
0
0
1
1
3
5
6
Provide tutoring
services
6
5
1
3
1
0
0
Prepare lessons
4
1
2
4
1
2
2
Conduct
seminars
7
2
1
4
0
2
0
Collect content
for coursework
2
2
2
4
2
2
2
Read eBooks
2
3
2
4
1
3
1
Take pictures
or make videos
for course
2
2
2
4
4
2
0
Other (please
specify)
5
11
0
0
0
0
0
Table 1: Mobile Device Use for M-Learning Activities for Teaching

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 56
https://isedj.org/; https://iscap.info
A Proposal for Combining Project Based Learning
and Lean Six Sigma to Teach Robotic Process
Automation Development and Enhance Systems
Integration
Dr. William H. Money
Department of Management and Entrepreneurship
Tommy and Victoria Baker School of Business
The Citadel
Charleston, SC 29409 USA
Dr. Lionel Q. Mew
School of Professional and Continuing Studies
University of Richmond
Richmond, VA 23173 USA
Abstract
This paper proposes a Project-based team instruction methodology with open-ended projects to teach
students critical analysis, design and implementation steps of developing Robotic Process Automation
(RPA) for information systems. The use of project-based learning is appropriate for teaching RPA
analysis and design with lean Six Sigma tools because of its experimental approach and documentation
of logical steps needed to learn how to implement RPA successfully. The approach systematically
documents work currently performed and defines future actions of the process while ensuring significant
benefits are achieved with the RPA enhanced process. This methodology is important because the
application of RPA is not commonly taught in Management Information System (MIS) programs. MIS
students may not understand the significance of combined methodology, RPA tool, and usefulness of
RPA until they enter the workforce where RPA is rapidly becoming available and easier to implement.
The lecture sessions and exercises are valuable because it is easy to communicate the value of RPA in
terms of time, quality, volume of transactions, etc. using Lean Six Sigma analytic approaches. The
exercises involve hands on activities to make this learning experience interesting for students to readily
associate the theoretical process improvement agreement and visualize the practical value of RPA
enhanced projects. The paper discusses the need for process changes (and new development
approaches) in organization to match the properties and functions within enterprise systems and ERPs
that has led to criticism of the enterprise systems. This criticism is attributable to the ERPs’ many sub-
functions and operations that have limited adaptability and reduced functional and operational flexibility.
The RPAs require limited prior knowledge of ERPs or their sub-processes for the improvements that are
made in the performance of the organization. Thus, students do not have to “learn” how these enterprise
or ERP systems operate to make changes or task improvements. This paper presents a project-based
methodology and design approach focusing on development of RPAs that help students learning how to
make the improvements using the RPS tools. The students learn that projects can deliver significant and
tangible benefits to organizations while engaging students in key activities of the analysis, design and
development process from a low code-no code perspective.
Keywords: Robotic Process Automation, Six Sigma, Project-based, PBL, Process

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 57
https://isedj.org/; https://iscap.info
1. INTRODUCTION
This paper proposes a Project-based team
instruction methodology for information systems
education using RPA. The discussion proposes
that a Project-based methodology can be used to
combine Learn Six Sigma and Robotics Process
Automation in an educational program. The
education value is to enable students to integrate
systems and improve wok processes without low-
code or no-code tools. It also provides a
literature-based history of the relevant concepts.
The objective is to improve students’ education
by teaching them how to advance performance
with analysis using lean six sigma techniques.
These techniques are applied to document and
target needed system improvements and
integration. Students can learn how to deliver
great benefits by performing functional system
tasks and enhancing operations as part of a PBL
development project.
RPA may be loosely defined as using software
technologies designed to facilitate devising and
managing software robots to behave like humans
when interacting with systems and software.
Here, we discuss how Lean Six Sigma and Project
Based Learning (PBL) synergistically add value
when combined to teach students RPA concepts.
Information Systems Integration
Systems integration is a critical part of enabling
the paradigm of using Lean Six Sigma and PBL to
yield value to development projects and
operations. Although it may be seen as a side
topic, a prerequisite for efficient collaboration
within and between organizations units is this
integration of information systems. Although it is
often viewed as simple from a holistic standpoint,
the inability of systems to interoperate remains a
consistent problem in the enterprise. As
information systems proliferate, opportunities for
IT systems integration have increased greatly,
and these must be leveraged to add value.
However, difficulties with integration continue,
due to a lack of systems interoperability and data
definition and formatting related problems.
Despite intensive research on integration issues,
organizations continue to encounter significant
challenges. Schmidt, Otto, & Österle (2010)
developed a research framework, categorizing
concrete integration cases from business
practices.
This framework was developed by examining
integration cases from the literature. The work
proposed 9 problem categories and 21 integration
problems plaguing those efforts. The authors
suggest that detailed problems inhibiting
integration vary by business segment, goals, and
roles. Semantics, data object heterogeneity, data
value mismatches and attribute differences also
affect these problems. The conclusion from this
work and the literature is that there are many
open integration challenges in the Information
Systems discipline (Schmidt, Otto, & Österle,
2010).
It can be seen from this discussion that while
there are many blocks and challenges to
integration, there are also an increasing number
of opportunities to foster improved integration,
and it is essential to consider these as we help
students develop skills using Lean Six Sigma and
RPA.
Low-code/ and No-code Tools
Low-code/no-code development approaches are
terms that describe the uses of software tools and
templates to integrate system and process
operations. No-code/base-code tool platforms
may be guided platforms with a drag-and-drop
process or more automated incorporating
machine learning services. (Villegas-Ch, García-
Ortiz, & Sánchez-Viteri, 2021). Low-code and no-
code approaches employ visual software
development tools and environments. Robotics
Process Automation (RPA) tools are categorized
among the low-code/no-code approaches. These
tools allow developers and end-users to select,
drag and drop application components. The
components are then connected with the
applications to create enhanced applications or
augment programs with previously unavailable
functionality.
The RPA technology may be seen as an evolution
of the low-code/no-code environments developed
following the Computer Assisted Systems
Engineering (CASE) tool failures of the 80’s and
90’s (Kuhn, 1989; Dias, 2017). RPA became a
development alternative because few case tools
were successful for complete database application
generation. The case tools were costly and
difficult to implement and maintain, requiring
extensive training for developers and systems
maintenance personnel (Schmidt, 2006). Jones
(2002) notes that as much as 70 percent of CASE
tools were not being used by the end of the first
year.
This generally accepted software failure figure
(believed to be based on the 1994 Standish Chaos
study) has been questioned by Glass (2005). He

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 58
https://isedj.org/; https://iscap.info
argues that the failure rate is assessed from
varying perspectives such as cost over runs,
functional performance, etc., and that the true
rates are even lower. Regardless, there is no
question that failure rates during this period were
sub-optimal.
RPA’s no-code characteristics and drag/drop
technology are similar to other low-code/no-code
development environments such as Mendix, a
low-code Model Driven Development (MDD)
platform that also grew from the Computer CASE
tools of the eighties and nineties.
Tools like these enable system development to
occur at higher levels of abstraction, generating
fully functional applications from a model driven
environment (Hailpern & Tarr, 2006). The higher
levels of abstraction are achieved by automating
and simplifying development steps using the
context of domain models. The tools employ
templates, generate code, and in many cases,
generate fully functional applications.
Hyun (2019) provides a useful example of this
approach with a discussion of an environment-
based low-code and no-code execution platform
and an execution method that combines hybrid
and native apps, offering the advantages of each.
The environment enables the use of iPhones,
Android devices, and operation templates. The
development platform is a visually integrated
environment that enables drag and drop
components by non-technical developers. The
environment to construct modules can be
dynamically loaded when called. The system
provides functionality for authentication, user
authorization, commerce, messaging, social
publishing, and vision.
Early releases of RPA sought to minimize coding.
Many of these tools are approaching a high level
of ease of use today. However, it is marketing
jargon to say that they are truly low code or no
code. The users of the early RPA tools were
required to incorporate logic and instruction
programming to complete the automation
process. Avoiding marketing jargon, the low-code
RPA automates straightforward processes
through a drag & drop user interface that
executes a user’s activities. Coded bots can still
complete more complicated or complex
processes. The low/no code tools are presently
used to complete and automate standard work
tasks, such as Excel operations, email responses,
report creation, and authorization recoding. Full
no-code RPA is currently not available or in use.
However, user prototyping and testing of RPA
tools can assess readily the ease of use and
amount coding required. Progress toward a more
complete low-code/no-code target environment
is being made.
Although the low-code/no-code development
approach has become an increasingly important
factor and tool for current software development
challenges, it is not always adopted. Global trends
do not always represent the popularity, adoption,
and use of the low-code/no-code development
approach. This was assessed in the Slovenian
environment with regard to one specific toolset,
Power Automate. The results showed that use of
this low-code/no-code development approach in
Slovenian organizations is low because of limited
usability and functionality concerns (Beranic,
Rek, & Heričko; 2020).
The need for RPA is couched in the integration
required to improve legacy systems regardless of
the environments available for system
operations. The movement of systems to the
cloud, combined with integration difficulties,
promulgates the lift/shift approach of cloud
migration. In this migration approach,
information systems and applications are
migrated into a cloud environment without
making process changes even when systems are
moved into cloud environments with available
resources (Engelsrud, 2019).
As seen in cloud-computing adoption, many large
organizations are struggling to obtain the full
value of the migration to the cloud. This is
because the cloud migration (especially lift/shift)
simply moves information systems to the cloud
without the integrating functions and possibly
transforming processes with new strategies
needed to obtain full cloud value. Utilities can
simplify the packaging, migration, and
deployment of applications for the cloud whether
the target is AWS, Google Cloud, Oracle Cloud, or
other cloud infrastructure.
However, without improvements or resolving
process integration concerns associated with
systems integration, taking legacy applications
and moving them to the cloud does not
automatically yield the benefits that cloud
infrastructure and support systems can provide,
because the work processes are still not
integrated. The information technology
architectures that are the result of these
migrations may be complex, difficult to manage,
and costly (Bommadevara, Del Miglio, & Jansen,
2018). It is critical that systems not be simply
migrated to the cloud, but that work processes be
integrated to the cloud infrastructure.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 59
https://isedj.org/; https://iscap.info
A PBL educational approach is an appropriate
teaching method for students who must learn
about cloud migration and how to integrate
systems. As PBL is implemented in the classroom,
students design, build and employ solutions to a
problem through a hands-on, collaborative
methodology. The true objective is to improve
performance with analysis using lean six sigma
techniques to document and target system
improvements that will deliver great benefits by
performing functional system tasks and
improving operations as part of the PBL
development project.
2. EDUCATION FOR INTEGRATION
To foster integration in their PBL projects,
students must understand the underlying
importance of the work and the task performed in
the processes to integrate systems. In large
projects and organizations with decentralized
work packages and task areas, it is important to
integrate properly the various outputs to provide
the customer with a coherent deliverable.
MIS students who join organizations that design
and support information systems see first-hand
how the work performed by organizational
information systems is subdivided into segments
for system execution, functional performance and
completion. This concept – the division of labor
(specialization) is evident in the segmentation of
systems that are consistently used by various
divisions, departments, and offices of
organizations.
The individual tasks contribute to productivity
increases by focusing effort on the tasks and data
used by each functional area. For example, in the
field of manufacturing, use of business
applications has expanded significantly over the
years. This expansion has increased both the
availability and volume of planning and execution
information for managers and decision makers.
The information enables decision makers to
assess and monitor performance at all levels of
the organization. Developed applications let end
users obtain predefined management reports
including information needed for managerial
execution. The information is of significant value
for strategic planning, increased productivity,
reducing service cycles, reducing product
development cycles, reducing marketing life
cycles, and increasing the understanding of
customer’s needs, thus facilitating business and
process reengineering (Sharma, 2012: 553). This
breaking up of work elements is essential to
delivering large projects. However, the breaking
up and decentralization make it difficult to
assemble and integrate tasks for a coherent
deliverable to the customer.
Managers and organizations remain faced with
the significant task of assembling and integrating
the divided work elements to produce the output
desired by the customer. Further, managers must
deal with migrating into business and
organization environments that lead to changes
in the data, knowledge information systems and
business strategy.
To gain the greatest benefit from information
systems, one must also understand the
relationship between knowledge and information
system strategies, and their overall impact on
firm performance. It is important that the
dynamic capabilities of knowledge strategy and
planning result in necessary changes in systems
to enable dynamic and innovative capabilities to
be developed.
Findings from a study of 234 Brazilian companies
support this logical argument. It finds
performance is positively impacted through
alignment between knowledge strategy planning
and information systems strategy. Managers
must recognize that the work of the firm is
dynamic, and that alignment between
information systems and the strategic actions of
the organization is important to success
(Yoshikuni, Galvão, & Albertin, 2021). It can be
deduced that knowledge and information system
strategies must also be reconciled and integrated.
Research and improvement attempts have
focused on business processes supported by
information systems (and the data, information,
and knowledge derived from the systems) for
many years. Business has been designing and
integrating processes as business and industrial
organizations evolve to offer systems that are
more complex, with useful data, insights, and
knowledge for decision makers. The systems also
seek to meet the information requirements of
highly complex stakeholder demands and
governance regulations.
It is therefore important for students entering the
workforce to understand these concepts in order
to integrate work segments and processes so the
information presents a coherent whole from a
holistically consistent system.
How to Integrate Systems in the Age of
Processes and Computerized Information
Systems
Porter and Millar (1985) discussed linkages
between computerized information systems and

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 60
https://isedj.org/; https://iscap.info
the integration mission, and projected a future
role that information technology would play in the
value chain. They argue that information
technology and information that businesses
create would enable management to employ this
information in executing work processes. These
combined factors provide an advantage derived
from the information-processing component that
executes steps required to capture, manipulate,
and channel the data.
This support enables managers to perform the
value chain activity. The data handling
improvements they describe are attributable to
barcodes for error handling reductions, databases
for knowledge and experience storage,
management of services with data, improved
weather satellite data uses, financial analysis
through data, transfer of data between suppliers
and manufacturers, data for improved designs for
manufacturing coordination, uses of office
support data, and communication data.
The value chain framework addresses the role of
computer information systems in achieving
helpful integration. White and Person (2001)
suggest this as a framework for integrating a
firm’s activities within a supply chain. They
recognize the requirements for integrating
customer service activities into the decision-
making process of manufacturing organizations.
These authors also discuss the dynamic nature of
the organization, and argue that just-in-time
computer systems and new product process
combine with information technologies to provide
the mechanisms for integration of the various
supply chain task activities.
The tasks and processes are conceptualized as
frameworks containing steps in a sequence. The
processes have many components, agents, and
outcomes.
The many authors and managerial perspectives
indicate that difficulties with the integration of
organizational processes have always been
challenging. As these references summarize,
within the last 40 years, information systems
implemented with electronic technology through
computer information systems and electronic
data processing technologies have been
“inserted” into this essential mission of
attempting to manage processes and their data,
and improve the coordination and integration of
the work within and between organizations. As
Schmidt, Otto, & Österle (2010) discuss, this
“levied” integration requirement for information
systems is a prerequisite for efficient
collaboration within and between organizational
units that results in substantial tasks.
Information systems have grown and become
ever more complex to meet the needs of large
organizations. The large category of enterprise
information systems has become standardized
with more carefully pre-defined data and
processes to meet broadly the needs of many
large organizations, and for wider marketability.
This tendency to force process changes on
organization (to match the properties and
functions within enterprise systems) has led to
criticism of the enterprise systems. This criticism
is attributable to their many sub-functions and
operations that have limited adaptability and
reduced functional and operational flexibility.
Information systems such as Enterprise Resource
Planning systems are caught in this dilemma. It
is exacerbated by the large enterprises and
matrix structures of originations that utilize
federation (decentralized control and local unit
development of some functionality) as their
information systems implementation approach.
The standardized enterprise systems are thus less
flexible and adaptive, and the decentralized
enterprises are incapable of exchanging and
making information available in many instances.
This creates a situation where managers lack
visibility into the results of processes, or where
data from one process are simply not accessible
to another work unit. A large adaptive enterprise
requires information systems to meet a business
strategy that can deliver information visibility
across the enterprise, and that are flexible for use
in new and innovative ways (Evgeniou, 2002).
Thus, integration is critical for the large
enterprise.
General Problem with Major Applications
The need for change after implementation was
addressed by Gattiker, & Goodhue, (2005). They
offer the theory, supported by their research, that
because these systems include data and effect
greater process integration, an ERP will be a
relatively better fit, requiring fewer changes,
when interdependence is high and differentiation
is low among/between the subcomponent of the
company using the ERP. If differentiation is high
at the subunit level of the organization (business
function or location, such as a manufacturing
plant) ERP customization will be required.
Further, the amount of time since ERP
implementation will increase the need for further
customization (supported by a large number of
manufacturing plants).

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 61
https://isedj.org/; https://iscap.info
A comprehensive discussion of ERP systems
published by Sheik, & Sulphey (2020) discussing
Enterprise Resource Planning (ERP) failures and
limitations over the past 20 years indicates that
implementation is still difficult, and changes after
implementation are still required. It identifies the
reasons for failures documented in numerous ERP
studies. The literature recognizes many types of
failures associated with information systems
project implementation, planning, management
support, culture and management process.
The work is useful because it notes that even
overcoming these issues does not assure success
for an ERP system or the organization seeking to
obtain value from this effort. These authors
discuss the tendency of organizations to
underestimate the efforts needed to handle
change in the organizations. In these initial
implementations, ERP systems can affect any
functional area of the company's basic business
model, and require systemic modifications.
Integration is required.
In discussing the problems in large scale ERP
implementations, research studies of integrated
supply chains show that effective operations and
integration are achieved by linking information
from suppliers, partners and customers within
and across national borders. This can be by
implementing information technologies and
systems such as ERPs to facilitate the desired
level and details needed for integration. There are
cases of successful and unsuccessful
implementations. The principal reason for failure
is often associated with poor management of the
implementation process (Sheik, & Sulphey,
2020).
This paper identifies the different types of issues
that can arise and require adaptation for ERP
systems within a large manufacturing
organization. The core issues to confront for
successful implementation of enterprise
information system according to this case study
were addressed by piloting a small portion of the
enterprise implementation to assess and
demonstrate how business principles, processes,
procedures, role definitions and behaviors (as
well as software, hardware and data transfers)
would influence the organization.
The initial problems experienced in the attempt to
go live included user authorization and clearance
levels, work routing and tracking (via cards),
incorrect data values existing between the legacy
systems and the new system, incorrect inventory
levels and WIP data, and incorrect MPR
transactions (Yusuf, Gunasekaran, & Abthorpe,
2004). They conclude that adaptation is
necessary throughout the development lifecycle.
User Developed Apps and Desktop Tools
Proliferate with Increased Workforce
Mobility
Development frameworks are necessary. Large
enterprise systems and changes are not the only
forces driving information systems today. User
empowerment, education, and the widespread
use of technology have influenced the
organizational end user. Workers are not afraid to
develop apps and seek to access information
needed in their work activities through user
development and the widespread proliferation of
desktop tools.
Coronado, Mastrogiovanni, Indurkhya, & Venture
(2020) addressed this increasing demand for
tools and expansion of interest in user developed
information systems. Individuals in social
situations will trust robots (automated programs
performing a work function or task) to execute
work in industries and in scenarios where the
robot is directed by an information system
(perhaps some form of AI) to interact with
humans. These authors surveyed user
development environments that might foster
application development involving robots with
social capabilities, features that could support
social research goals, and serve professional
employees not educated or trained in more
traditional programming languages and
techniques.
The work identified and assessed sixteen
programming environments with modeling
approaches, Component-Based Software
Engineering, and web technologies. The research
found that few of the environments enable end
users to be independent from high-tech support.
Their work calls for objective and comparative
evaluations, usability studies, and design
validations of the tools for designing working
applications. Engaging robot-based applications
requires the availability of usable, flexible and
accessible development frameworks that can be
adopted and mastered by practitioners who are
truly adult end users.
3. METHODOLOGY
This educational experience applies a Project
Based Learning (PBL) approach to the learning
experience. In project-based learning the
instructional focus is student-centered. The
experiences are based the principles that (1)
learning is context-specific, (2) learning
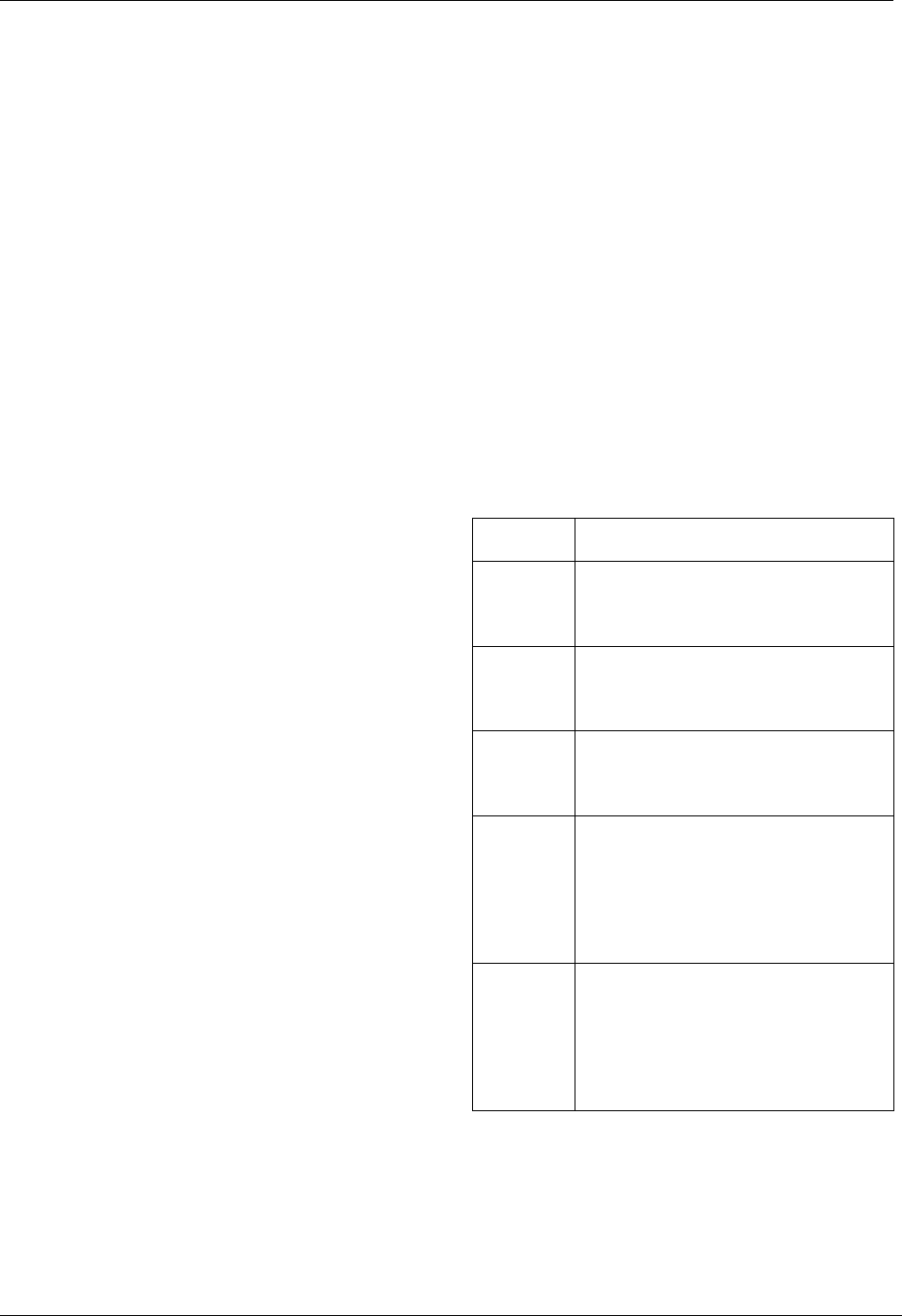
Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 62
https://isedj.org/; https://iscap.info
processed actively involved those learning, and
(3) goals are reached through social interactions
and Knowledge sharing (Jalinus, Nabawi, &
Mardin, 2017, September; Cocco, 2006). It is
considered to be a particular type of inquiry-
based learning where the context of learning is
provided through authentic questions and
problems within real-world practices
The learning experience is agile based. It involves
an introduction to the requirements for changes
and adaptations for enterprise information
systems, data and process integration, and the
continued need for user developed applications
that work in the desktop environments and in
mobile applications. In this paradigm, use of Lean
Six Sigma in the analysis and development
sections of the PBL project adds value and
improves integration.
Analysis: Lean Six Sigma Designs Steps for
Value
The goals of improving flexibility and supporting
operations have contributed to the Six Sigma
approach to process improvement and selecting
changes to implement in organizations. It is a
strong foundation for improvements and
innovations because it involves doing the work
better and actually improving the work to be
accomplished in many instances. It is applicable
to processes used to produce products and
services, expand markets, and deliver operational
performance. The work focuses on customer
needs, detailed data analysis and facts about
performance levels, errors, and required actions.
Analysis of organization results derived from the
application of Six Sigma programs show
improvements in broad-based innovation and
financial performance. The key characteristics of
these approaches include an improvement -
innovation vision based on data (from customers,
insights, and analytic studies), clear objectives,
organizational commitment to the change
objectives or vision, alignment across the
organization, training, and target processes to
demonstrate the Six Sigma program.
Lean Six Sigma is a combination of lean methods
(analysis, documentation, and analytic tasks that
are performed within the organization) and Six
Sigma approaches that organizes the tasks in an
understandable and executable fashion. Lean Six
Sigma utilizes knowledge (from the experience of
many organizations that have followed the
approach), methods designed to elicit specific
data and understanding of activities and
operations, and tools derived from operational
improvement research and implementations.
The lean portion of the approach targets cost
reductions through process optimization. The six-
sigma portion focuses on meeting customer
needs and stakeholder expectations. It seeks to
improve quality, via measurement and defect or
error elimination. This is accomplished by both
eliminating the opportunities for errors in a
process and improving the steps, materials, and
performance of a task. The simultaneous goals
are to achieve both effectiveness and efficiency
(Byrne, Lubowe, & Blitz, (2007).
There are five major steps in a lean six-sigma
process as shown in table 1. It is labeled
“DMAIC”, an acronym for the five sequential
phases: Define-Measure-Analyze-Improve-
Control. These phases flow logically from defining
a problem through implementing solutions. The
changes introduced are directly associated with
causes (George, Maxey, & Upton, 2004).
Step
Name
Value
Design
Review, validate charter; define:
customer, problem, benefits
sought, financial objectives, plan,
schedule
Measure
Build value stream map, inputs,
operational definitions, data
collection plan, measurements,
process capability, measure gate
Analyze
Determine critical inputs, potential
root causes, reduce root cause list,
estimate root cause effects on
outputs, prioritize root causes
Improve
Develop potential solutions,
analyze and evaluate solutions,
develop “To-Be” value stream
map, develop pilot solution,
confirm attainment of project
goals, develop full scale
implementation plan
Control
Implement mistake proofing,
SOPs, training. Set process
controls, implement solution and
on-going process measurements,
develop opportunities to apply
project lessons, transition to
monitoring control office
Table 1. Summarized Lean Six Sigma Steps
Analysis Results: A New Process Design
The result of the analysis using the steps outlined
is a process that will perform more effectively and
efficiently. Further, the approach and tools
employed document the pre – post outcome

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 63
https://isedj.org/; https://iscap.info
metrics that will be used to demonstrate to
stakeholders that there are real benefits and
improvements from the process changes.
4. RPA: IMPLEMENTING THE AUTOMATION
The objectives of this learning experience are to
deliver students a clear understanding of the
technology and methods. Students will
understand the actions and sequence of steps
needed to apply lean six sigma methods and RPA
tools that enhance processes and information
systems. The lessons focus on RPA tools (after a
full analysis) and use various product offerings to
provide a hands-on set of educational exercises.
This section discusses RPA and how the tools
implement the designs documented. It also
provides an overview of the tools that will be used
in the exercises.
Robotic Process Automation
This paper argues that Robotic Process
Automation (RPA) is a recent improvement
(evolving in the past ~10 years) in computer
information systems. This technology is applied in
organizations to achieve integration between
systems and to perform mundane and repetitive
tasks without altering or modifying the
information systems that are the targets or
sources of the data required. RPAs execute rule-
based, routine, and predictable tasks in
combination with structured, understood, and
stable data in a semi-automated and automated
manner. (Primer, 2015).
RPA Functionality and Operation
How does RPA perform integrative and productive
tasks? RPA moves data and information
seamlessly between systems and processes. RPA
technology can be implemented across many
functions. It is a practical linkage technology for
many different process focused tasks (definable,
repeatable, and rules-based). It can be optionally
executed at the explicit direction of employees
and can therefore assist them in their work. RPA
can assist with diagnosing when decisions are not
always clear (the data do not legitimately fit) and
the business rules-base is not complete for all
situations (present and those introduced by
business changes). In these instances, the “error”
or unaddressed states can be recorded and
handed directly by the user. New “rules” or
actions can be added to the RPA automation to
handle the situation when it is encountered in the
future.
RPA has multiple operating modes. It can function
in attended mode where an employee “triggers”
the bot for day-to-day operations or
automatically with the employee watching for
exceptions and alerts (correct execution or failure
to execute). The bot can also function in an
“unattended mode” on a server based on user-
determined triggers such as a date and time. For
example, a bot could be programmed to trigger
automatically to execute at 12:00 a.m. on Friday,
or when 1,000 cases have been received in a
queue. Thus, the RPA bot can serve as an
independent automated process that does not
demand human intervention in order to execute a
work process. It can make or execute a decision
if all the data and rules are clear and the outcome
decisions are predetermined.
RPA is very adaptive and fits many situations
because of its internal capabilities. The RPA has
several essential features that provide it
competencies beyond those found in code written
for scripting, screen scraping, and sequential
process management. 1) RPA development
utilizes straightforward dropping and dragging via
icons that represent steps in a process. RPA
process code is then produced automatically
without extensive programming, computer
training or expertise. 2) The RPA bot accesses
data produced by other computer systems or
programs. It emulates exactly how an employee
accesses this data (because the bot is created to
do just this task). 3) RPA has important security
and operational controls.
The RPA assumes only that logon ID and
password of the user. This is required to access
what is normally seen or obtained by the worker
from the target or other system’s presentation
layer. Therefore, the RPA bot is non-interfering or
invasive for organization work beyond the explicit
instructions executed by the bot’s design. 4)
Finally, RPA is a secure and scalable technology
that executes on the enterprise-protected
platform. It can be configured, audited, and
managed at the enterprise or organizational level
that utilizes this technology.
The output of a bot appears to be the product of
code that functions “like a macro,” but with more
capabilities, options, and functionality that is not
restricted to an application like Word or Excel. It
can be visualized as a very smart, tireless, and
sophisticated desktop assistant. The bot appears
as a powerful worker or “aid” that performs
scripting and screen scraping (record and replay),
acts quickly, and is able to record (without error)
what it is doing. The bot replicates the assigned
task repeatedly (tirelessly) – like a true robot. It
is trained by watching a user’s selections (of data
or decisions), recording mouse clicks, matching
inputs from the keyboard and completing the

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 64
https://isedj.org/; https://iscap.info
process as the user does. However, the bot is not
intelligent – and does not know why it is doing
this work since it only performs the assigned set
of actions when called upon. (Madakam,
Holmukhe, & Jaiswal, 2019; Peláez, & Kyriakou,
2008; Schmitz, Dietze, & Czarnecki, 2019).
RPA Products
Product
Provider
Product name and
Description
Power
Automate
Power Automate is a business
tool (Microsoft code) that
automates business processes,
sends task reminders, move
business data between systems
on a schedule, connects data
sources or and publicly available
APIs, can automate tasks on a
local computer.
Automation
Everywhere
Automation Anywhere consists
of three core components – Bot
Creator (drag and drop method
to create rule-based
automations), Control Room
(hub for RPA robots start,
paused, stop, or scheduling),
and Bot Runner (run robots.
provides the end-to-end status
of the bot’s execution back to
the control room). The core
components are used in tandem
to build and deploy a successful
automated workforce.
UiPath
UiPath offers complex and
highly featured automation for
more complex automation
products (standalone end user -
not integrated, hosted – on
premise, cloud) corresponding
to the user deployment
requirements. Products include
two development environments
– Studio and StudioX (with
limited capabilities),
automations called assistant
(bots), and an Orchestrator for
management and control of the
assistants. The cloud and hosted
product link together and can
exchange data when installed as
Automation Suite.
Table 2: RPA Tools
There are a number of RPA products available in
the market today. Three examples of these tools
are provided in Table 2 to help students, readers
and businesses understand the varying
capabilities that can affect the choice of a tool for
specific industry and target process. Students can
use the prosed methodology with any of the tools.
However, the ability of the tool to perform more
complex task automation will depend upon the
capabilities and functions available in a specific
tool.
5. Project Based Learning (PBL)
EDUCATION EXPERIENCE
What is Project Based Learning (PBL)?
Project-based learning (PBL) is a learning
experience that engages students in experiential
activities. The students are able to learn and
develop skills while working in teams. This
teaching approach stresses real-world projects
that can be understood readily and have
significance for the students. Larmer &
Mergendoller (2010) propose the project be a
task that matters and one that the students will
want to do well. The project must be well
designed and well implemented to serve its
educational purpose.
Larmer & Mergendoller (2010) propose seven
essential characteristics for these PBL
experiences. The criteria listed in Table 3 are
conceptual ways of engaging students in the
exercise.
Table 3: Essential Exercise Characteristics.
Amaral (2021) described how projects taught by
using the PBL approach could have different
goals, and actively involve students so they get
their hands dirty. This work notes that students
might learn and discover skills and materials
required to complete the project. They will also
reassess their learning process at the end of a
project.
Value of PBL
The project technique is effective in imparting the
1
A Need to Know
Relevance of the information
2
A Driving Question
How to improve, reduce,
speed up, etc.
3
Student Voice and Choice
How to reduce tedium,
improve situation, minimize
errors),
4 21st Century Skills
Collaboration,
communication, sharing
5
Inquiry and Innovation
Gathering information,
alternatives, suggestions for
improvement
6
Feedback and Revision
Critiques, reviews,
examinations of project work
7
Publically Presented Product
Exhibit and present the
solution
(Larmer & Mergendoller, 2010)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 65
https://isedj.org/; https://iscap.info
educational understanding and hands-on learning
experience to students. Alacapınar (2008) assess
how the delivery of a course using the project-
based learning technique affects student opinions
on cognitive, affective and psychomotor domains
using questionnaires and semi-structured
interviews. The results report on project
technique effectiveness. The interview feedback
results are that the project technique enhanced
student creativity, helped them acquire high-level
information, target domain skills, appreciation of
group work and collaboration, and that separation
into groups during the work consolidated affinity,
trust, and friendship.
How PBL Works for Lean Six Sigma and RPA
The projects used in the class sessions apply the
seven essential project design elements as a
framework. The interesting and relevant problem
is how to complete the work required of an
administrative assistant in demanding situations.
The situations are those where the work is
tedious, repetitive, with manual steps, error
prone and required to have very high accuracy.
The work may also require display, moving (copy
or cut/paste), reformatting and/or validating
data submitted by emails, and through
spreadsheets, and audits with summary
reporting.
The project is meaningful for students because it
is work derived from real world tasks, and
essential to the job and eventual promotion. The
project deliverable is a working system utilizing
the RPA tool.
Appendix A lists the steps a student will execute
to complete the analysis, design, and coding of
an automation (bot) using two different RPA
tools. The first exercise provides the steps for the
use of Power Automate, a simpler and easier to
use RPA tool with basic product features. The
second exercise utilizes UiPath Studio to perform
the task. This tool has more features and
functionality. Appendix B lists the task actions a
student will execute to complete an RPA project
with straightforward output objectives. Appendix
B task actions can be perfumed with either tool.
6. CONCLUSIONS
This paper describes the use of project-based
learning to teach design skills for RPA
development to management information system
students. A Project-based team instruction
approach is followed using open-ended projects
to teach students critical analysis, design, and the
implementation steps of developing Robotic
Process Automation (RPA) for information
systems. It describes why the project-based
learning method is appropriate for teaching RPA
analysis and design, and uses lean Six Sigma
tools to perform the analysis needed to support a
low-code/no-code development project. Lean Six
Sigma is an important analysis step because of its
analytical approach and complete documentation
of logical steps needed to understand how to
select and implement successful RPAs. The
general issues considered in the design of class
sessions emphasize the use of Lean Six Sigma
and RPA in improving organization tasks.
Consideration of the literature on the application
of PBL suggests many skills, including problem
solving, task design innovation, group-work and
collaboration skills desired by employers can be
improved with this approach. The paper discusses
factors involved in the development of problem-
based leaning (PBL) sessions, and summarizes
exercises planned for the educational experience.
7. REFERENCES
Alacapınar, F. (2008). Effectiveness of project-
based learning. Eurasian Journal of
Educational Research, 32(1), 17-34.
Amaral, J. A. A. D. (2021). Using project-based
learning to teach project-based learning:
lessons learned. Pro-Posições, 32.
Beranic, T., Rek, P., & Heričko, M. (2020).
Adoption and usability of low-code/no-code
development tools. In Central European
Conference on Information and Intelligent
Systems (pp. 97-103). Faculty of
Organization and Informatics Varazdin.
Bommadevara, N., Del Miglio, A., & Jansen, S.
(2018). Cloud adoption to accelerate IT
modernization. McKinsey Digital.
Byrne, G., Lubowe, D., & Blitz, A. (2007). Using
a Lean Six Sigma approach to drive
innovation. Strategy & Leadership.
Cocco, S. (2006). Student leadership
development: The contribution of project-
based learning. Unpublished Master’s thesis.
Royal Roads University, Victoria, BC.
Coronado, E., Mastrogiovanni, F., Indurkhya, B.,
& Venture, G. (2020). Visual programming
environments for end-user development of
intelligent and social robots, a systematic
review. Journal of Computer Languages,
58(June 2020), 100970.
Dias, G. K. A. (2017). Evolvement of computer
aided software engineering (CASE) Tools: A
user experience. International journal of
computer science and software engineering,

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 66
https://isedj.org/; https://iscap.info
6(3), 55.
Evgeniou, T. (2002). Information integration and
information strategies for adaptive
enterprises. European Management Journal,
20(5), 486-494.
Engelsrud, A. (2019). Moving to the Cloud: Lift
and Shift. In Managing PeopleSoft on the
Oracle Cloud (pp. 229-242). Apress,
Berkeley, CA.
Gattiker, T. F., & Goodhue, D. L. (2005). What
happens after ERP implementation:
understanding the impact of interdependence
and differentiation on plant-level outcomes.
MIS quarterly, 29(3),559-585.
George, M. L., Maxey, J., Rowlands, D. T., &
Upton, M. (2004). Lean six sigma pocket
toolbook. McGraw-Hill Professional
Publishing.
Glass, R. L. (2005). IT failure rates-70% or 10-
15%? IEEE software, 22(3), 112-110.
Hailpern, B., & Tarr, P. (2006). Model-driven
development: The good, the bad, and the
ugly. IBM systems journal, 45(3), 451-461.
Hyun, C. Y. (2019). Design and Implementation
of a Low-Code/No-Code System.
International journal of advanced smart
convergence, 8(4), 188-193.
Jalinus, N., Nabawi, R. A., & Mardin, A. (2017,
September). The seven steps of project-
based learning model to enhance productive
competences of vocational students. In
International Conference on Technology and
Vocational Teachers (ICTVT 2017) (pp. 251-
256). Atlantis Press.
Jones, W. (2002). Case tool time.
https://scholar.google.com/scholar?hl=en&a
s_sdt=0%2C41&q=%22CASE+Tool+Time%
22++MSIS+488+Fall+2002++Walt+Jones&
btnG= Last accessed: June 2, 2022.
Kuhn, D. L. (1989). Selecting and effectively
using a computer aided software engineering
tool (No. WSRC-RP-89-483; CONF-891192-
7). Westinghouse Savannah River Co., Aiken,
SC (United States).
Larmer, J., & Mergendoller, J. R. (2010). Seven
essentials for project-based learning.
Educational leadership, 68(1), 34-37.
Madakam, S., Holmukhe, R. M., & Jaiswal, D. K.
(2019). The future digital work force: robotic
process automation (RPA). JISTEM - Journal
of Information Systems and Technology
Management, 16.
Peláez, A. L., & Kyriakou, D. (2008). Robots,
genes and bytes: technology development
and social changes towards the year 2020.
Technological Forecasting and Social Change,
75(8), 1176-1201.
Porter, M. E., & Millar, V. E. (1985). How
information gives you competitive advantage.
Primer, A. (2015). Introduction to Robotic Process
Automation. Institute for Robotic Process
Automation.
Schmidt, A., Otto, B., & Österle, H. (2010).
Integrating information systems: case
studies on current challenges. Electronic
Markets, 20(2), 161-174.
Schmidt, D. C. (2006). Model-driven engineering.
Computer-IEEE Computer Society, 39(2), 25.
Schmitz, M., Dietze, C., & Czarnecki, C. (2019).
Enabling digital transformation through
robotic process automation at Deutsche
Telekom. In Digitalization Cases (pp. 15-33).
Springer, Cham.
Sharma, N. K. (2012). Management information
system. International Journal of
Management, IT and Engineering, 2(8), 553-
570.
Sheik, P. A., & Sulphey, M. M. (2020). Enterprise
Resource Planning (ERP) As a Potential Tool
for Organizational Effectiveness. Webology,
17(2).
Villegas-Ch, W., García-Ortiz, J., & Sánchez-
Viteri, S. (2021). Identification of the Factors
That Influence University Learning with Low-
Code/No-Code Artificial Intelligence
Techniques. Electronics, 10(10), 1192.
White, R. E., & Pearson, J. N. (2001). JIT, system
integration and customer service.
International Journal of Physical Distribution
& Logistics Management, 31(5), 313-333.
Yoshikuni, A. C., Galvão, F. R., & Albertin, A. L.
(2021). Knowledge strategy planning and
information system strategies enable
dynamic capabilities innovation capabilities
impacting firm performance. VINE Journal of
Information and Knowledge Management
Systems, 52(4), 508-530.
Yusuf, Y., Gunasekaran, A., & Abthorpe, M. S.
(2004). Enterprise information systems
project implementation: A case study of ERP
in Rolls-Royce. International journal of
production economics, 87(3), 251-266.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 67
https://isedj.org/; https://iscap.info
8. Product Appendix A
Product Exercise - Simple Exercise – Power Automate.
Tool Action Summary:
• Sign up and obtain Documentation. Sign up and sign in - Power Automate
• Power Automate, you can explore a diverse set of templates and learn about the key features
for Power Automate. You can get a quick sense of what is possible and how Power Automate
could help your business and your life.
• Analyze the desired process, to find an appropriate template (e.g., templates for sending you a
text message, adding Twitter leads, backing up files...)
• Analyze the tasks and set conditions that trigger the flow and the action that result from that
event (adjust, add, or delete actions).
• Select an appropriate flow type based upon the Lean Analysis (cloud flow, desktop, business
process, etc.
• (Optional) Examine code by viewing code generated for all actions and triggers (for a clearer
understanding of the data that's being used by triggers and actions) [Action or trigger > Peek
code].
• Select a connector. Connectors are proxies or wrappers around an API that allows the underlying
service to talk to Microsoft Power Automate. A user connects to build their app and workflow
from software as a service (SaaS) connectors. This connects apps, data, and devices, etc.)
• Test and validate that the new actions and data were created.
• Execute or Run the new workflow. After creating and tested a desktop flow, run it from an event,
schedule, or button.
• Manage the flow in Power Apps > select Flows in the left navigation pane
Product Exercise – Complex Exercise – Power Automate.
• Install the UiPath Studio (development tool) from UiPath, or local network.
• Enter required information (name device ID – if not present, > Activate
• 2. Open and select a project, activity (press a key, enter a number, etc.) and sequence
(combined task) designation.
>Choose from: Plan, Simple (template/flow hart – for different sequence of activates), Agent
(shortcut for improvement), Transactional (uses states – e.g., loading, execute shut-does – not
moving until all tasks for the project are completed
• Build the project. Create a name,
Add a function (record, scrape, user event, value), >Run, test
Scrape (screen or web), user event (keyboard or mouse entry). Set variables
Create file (separate parts of the automation)
Activity – drag and drop into the activity program (pane).
• Domains (7) – UI domain – keyboard, mouse. (drag/drop activates according to the project
logic),
• User events (triggers); orchestrator – depending upon edition; system (delete, open); condition
programs (fi. Else); workflow - sequencing
• Properties – set addresses, locations
• Control bar – Used to create the components for variables, arguments, imports.
• Create an automation.
• Test and install in production

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 68
https://isedj.org/; https://iscap.info
9. Project Activity Appendix B
1. Create file output from Excel (Task assignment, Excel file, output required)
2. Create email upon task completion. (Task assignment, Excel (or other source file), email
message - output required)
3. Create message of data arrival, update file. (Trigger for automation, Excel (or other record
file), email message - output required)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 69
https://isedj.org/; https://iscap.info
Teaching Case
Alexa, Help Me Learn About the Internet of Things!
Mark Frydenberg
Computer Information Systems Department
Bentley University
Waltham, MA 02452, USA
Abstract
The Internet of Things (IoT) is a network of objects that can exchange data with other devices also
connected to the Internet. One of the most common consumer examples of IoT is home automation, as
a variety of smart devices, including doorbells, lightbulbs, thermostats, and refrigerators are now
available which users can control remotely using mobile apps or smart speakers. In this hands-on
activity, students will apply their basic skills in accessing wireless networks and using mobile devices to
connect an Amazon Echo smart speaker to a home network, configure smart plugs to communicate with
the Echo, and develop routines to interact with the smart plugs, smartphones, and other smart devices.
Keywords: Internet of Things, Amazon Echo, Automation, Digital Literacy, Active Learning
1. INTRODUCTION
The Internet of Things makes it possible to
connect devices in everyday objects, often
equipped with software and sensors, to send and
receive data over the Internet. Devices have an
IP address allowing them to connect to the
Internet, usually through a wireless network,
enabling communication between other
connected devices. A smart device is one that can
connect to the Internet.
An Amazon Echo (“Echo”) is a smart speaker
developed by Amazon that is commonly used in
homes to perform automated tasks and control
smart devices. Echo devices are widely available
in a variety of formats, including audio speakers
(Echo Dot), video displays (Echo Show), devices
to connect additional sensors (Echo Flex), and
devices for use in vehicles (Echo Auto).
Echo devices use the Alexa intelligent personal
assistant service to respond to a user’s voice
commands, that typically begin with the wake
word, “Alexa.” Users commonly interact with
Alexa to set alarms and timers, perform Internet
searches, play music, manage lists, and obtain
current news and weather information. Alexa
skills are software modules that perform tasks
such as playing games, setting timers and
reminders, and listening to music or audio books.
Alexa routines are sequences of tasks that you
can configure to perform in response to a voice
command.
Echo devices can connect to several smart
devices to perform home automation tasks, such
as turning on and off lights and adjusting
thermostats.
In this lab activity, you will interact with the
Internet of Things by connecting an Echo device
to a wireless network. You will control smart
devices using mobile apps and voice commands,
and create skills and routines to automate tasks,
add capabilities, and perform actions when
triggered by specific events.
If you do not have access to an Echo or Alexa-
enabled device, you can use the Alexa mobile app
on a smartphone or tablet to complete the steps
in this activity that specifically do not refer to
configuring or interacting with an Echo device.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 70
https://isedj.org/; https://iscap.info
Learning Objectives
By completing this lab activity as part of your
information systems / technology literacy course,
you will be able to:
• Define what is meant by the Internet of
Things (IoT)
• Describe how to accomplish home
automation using connected devices
• Control smart plugs or devices using a
smart phone and the Alexa personal
assistant app on your Amazon Echo
• Identify sources of data and providers
that can share data over the Internet.
• Create routines with Amazon’s Echo to
automate home tasks
• Describe the role of a home network in
connecting devices
• Explain the role of APIs (application
programming interfaces) in sharing data
2. THE AMAZON ECHO
INTERNET OF THINGS LAB ACTIVITY
Prerequisites
While no programing knowledge is required to
complete this activity, several digital literacy and
information technology skills are required:
• Create, edit, and share a document on
Google Drive or OneDrive
• Capture and share screenshots from a
computer or mobile device
• Transfer files from a mobile device to a
laptop using cloud storage
• Create a video using your computer or
mobile device
• Connect a computer or mobile device to a
wireless network
• Locate a device’s MAC and IP address
Preparing For The Activity
You will work in teams of three or four to
complete the activity. Each person in your team
will have a different role, so decide who is going
to do what. It is fine to change roles throughout
the project so each person can experience more
than one role.
• Reader: Reads the instructions aloud at
each step for the group to discuss and
conduct
• Recorder: Summarizes the group’s
conversation about each task or
discussion question in the lab report
• Connector: Downloads apps to smart
phone, connects and configures devices
• Multimedia Producer: Records video,
photos, and gathers screenshots and
other multimedia as required
Your group will create a shared online document
or presentation to contain your screen shots and
answers to several discussion questions. Your
group also will create a short video and post it to
Flip, a collaborative video recording and sharing
platform, to demonstrate that your connected
devices and routines function correctly when you
speak voice commands. (Visit http://flip.com.)
You can work together on the project, but each
student should reflect their own learning and then
answer the open-ended questions individually.
Also consider the technology skills you used when
completing is activity.
Complete these steps before working on this
activity:
• Read this description before coming to
class so that you will be familiar with the
steps required. Doing so will save time
when you work on this in class!
• Identify three or four group members
• Create a lab report document on Google
Drive or OneDrive as directed by your
instructor. Share it with your instructor
and the members of your group.
Equipment
Your instructor will provide the equipment as
shown in Figure 1, for your use during this lab
activity:
• An Echo Dot smart speaker
• A smart plug (outlet)
• A light switch socket
• A lightbulb
Figure 1. IoT Lab Equipment
You will also need a laptop and smartphone. You
will need access to the network name and
password on a wireless router.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 71
https://isedj.org/; https://iscap.info
3. COMPLETE THE LAB ACTIVITY
To complete this lab activity, you will accomplish
these tasks:
• Install the necessary apps on your phone
• Connect your Echo as a device on a
wireless network
• Set up a smart plug with an app on your
phone to turn on/off a light
• Set up Amazon Echo to turn on/off a light
using a voice command
• Create a routine for Alexa to follow
• Interact with and respond to external
data or events using If This Then That
• Bonus: Use Amazon Blueprints to create
custom skills
Set Up Your Phone
One person in each group, the “Connector”,
should download and install the mobile app for
the smart plug, and the Alexa app on their phone.
Install the Alexa app on your phone so you can
configure your Echo device. If using GoSund
smart plugs, download the SmartLife App. If
using Amazon brand plugs, you can use only the
Alexa app. Figure 2 shows the icons for the apps
to locate in your app store:
Figure 2. Alexa and SmartLife App icons.
If using other third-party smart plugs, download
the app associated with those plugs.
Create an Amazon Account
If a member of your group already has an Amazon
account, please feel free to sign in with your
personal credentials that you use with your own
Echo. After the completion of this lab activity, you
will remove the Echo device used for this project
from your account.
Open the Alexa app. If no one in the group has
an Amazon account, create a new Amazon
account for this activity (which you can delete
later). You should not need to provide a credit
card or phone number. Search for instructions
online for how to set up an Amazon account
without having to provide a credit card.
Configure the Smart Plug
These steps describe how to configure a third-
party smart plug using its app installed from the
Google Play or Apple App Store.
Connect your phone to the wireless network on
your router. (If you are configuring the router
yourself, set an SSID and password. If your
instructor is providing one router for the entire
class, use the SSID and password provided. Do
not connect to the 5G Network.
Open the app associated with your smart plug.
For GoSund plugs, open the SmartLife app. For
Amazon plugs, use the Alexa app; for other third-
party plugs, follow similar steps using their app,
Create a new account in the app using the same
credentials as the Amazon account. In the app,
allow permission for the app to access your
location, then identify the device (“socket/wifi”)
you want to add to the network, as shown in
Appendix I, Figure 5.
Enter the wireless network name and password to
connect the device to the network. Then follow
the instructions on the app to set up the plug as
shown in Appendix I, Figure 6. You will need to
press and hold the RESET button on the plug,
watch for a blinking light, and then check the app
to ensure that the plug connected to the Wi-Fi
network.
Note: When doing this step in a classroom with
other groups at the same time, make sure that
only one group’s plug is in set-up mode at a time
(The RESET button is blinking). Otherwise, the
app will connect to all plugs that are in set-up
mode. If one team is setting up their plug, wait
until they have finished, and then proceed with
configuring yours (by pressing the RESET button
for 5 seconds again).
Once connected, plug the light switch containing
the lightbulb into the smart plug. Test turning on
and off the light switch using the app, as shown
Appendix 1, Figure 7.
To verify the plug has an IP and a MAC address,
click ‘Mini Smart Plug’ in the app, click the pencil
icon in the top right, then click Device Settings to
see the IP and MAC address.
Set Up Amazon Echo
Install the Amazon Alexa app to your phone if you
do not have it already or sign out from your
personal Amazon account.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 72
https://isedj.org/; https://iscap.info
Press and hold the action button on the Echo Dot
(the solid circle button) until an orange ring
appears putting you in setup mode.
Follow steps in Alexa app to configure the device.
In the Devices tab, click the ‘+’ button in the top
right corner. Click Add Device, locate Amazon
Echo and your model. Select the wireless network
and enter its name and password. Follow the
prompts to choose a language, set the device’s
location, and skip through any introductory offers
or videos that appear while configuring the
device. in your home. See the screenshots in
Appendix 1, Figure 8.
Set Up Echo To Work With The Smart Plug
In your smart plug’s app, select the device, and
look for a third-party control option. Select Alexa
and sign in with your Amazon credentials to allow
access.
In the Alexa app, click Devices, click the ‘+’
button to add a device, and select the brand of
your plug. Click Discover Devices, and Alexa will
look for devices and connect to the plug. Note:
For GoSund plugs, choose SmartLife (not
GoSund).
Give the device a name (such as “Red Light”).
Speak the command to ask Alexa to turn on or off
the Red Light and verify that it works.
Set Up A Routine
A routine is a set of steps to perform when you
speak a trigger word, such as “good morning.”
You might have Alexa perform several actions in
sequence, such as turn on the light and play
music, news, traffic, or weather when you say
“good morning.” Follow the instructions at
https://www.amazon.com/alexa-routines/ to
build your own routine. Then save and test your
routine.
Automation with If This Then That
If This Then That (ifttt.com) is a web-based or
mobile development platform that allows you to
build automation applets that connect data from
different sources without writing any code. IFTTT
hosts more than 700 apps and services to
integrate data from social media sites, a few of
which are shown in Figure 3.
You can access IFTTT in a browser or by installing
the IFTTT app from Google Play or Apple’s App
Store. The free plan allows you to create up to
five applets. One person from each group should
install the IFTTT app on their phone and create an
account.
Figure 3. IFTTT Services
To create an applet, select a trigger condition (“if
this”) that needs to be true for the associated
action to run. For example, you can check if the
light connected to your smart plug is turned on.
Next, create the action (“then that”) to run when
the trigger condition is true. Select “Phone Call”
and enter your phone number to create the action
to call your phone when the trigger condition is
true. IFTTT will verify your phone number by
calling it and sending you a code to enter.
Test the applet by asking Alexa to turn on the
light and wait momentarily for your phone to ring.
Follow the steps in Appendix 1, Figure 9 to create
an applet that calls your phone when the light is
turned on.
Using this as an example, make your own applet
using IFTTT.
You should be able to configure your Echo and
smart plug and create a routine and an
IfThisThenThat applet during one 60-minute class
period. After completing these tasks, create a
short video introducing your group members, and

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 73
https://isedj.org/; https://iscap.info
demonstrating the voice commands, routines,
and applets that your group created.
Create Your Own Alexa Skills With Amazon
Blueprints (Extra Credit)
Alexa skills are applications that run within the
Alexa app. Amazon provides an on-line tool called
Amazon Blueprints to simplify the process of
creating skills to leave messages for people at
home, play quizzes, flashcards, and games, tell
stories, create custom news briefings, and more.
You can select a template for the application type
you wish to create, such as a multiple-choice
trivia quiz, and then add the information that you
would like to use in your game. After testing your
skill, you can share or publish your skill so others
can use it. For an additional challenge, use
Amazon Blueprints to create your own Alexa skill.
Try this in class if you have time or complete it
outside of class.
Visit https://blueprints.amazon.com/, as shown
in Figure 4, to create your own Alexa skills by
selecting and customizing one of the templates.
As you complete your skill, consider the steps
involved in creating, testing, and deploying it, and
how they relate to publishing software.
Clean-Up
If you are no longer going to use the Echo and
smart plug devices, remove the devices from your
Amazon account. In the Alexa app, select the
Echo device and deregister it from your account.
Remove the smart plug from your account.
In the Smart Life app, select the plug and remove
the device.
Uninstall any unwanted apps that you added to
your phone for this activity.
Reset your Echo device to factory settings. For 2
nd
Generation Echo devices, press the microphone
on/off and volume down buttons at the same time
until the light ring turns orange. Steps may vary
for other models of Echo devices.
In addition to the video showing that your devices
worked properly, create a lab report document
online and share it with your group members and
your instructor. Your lab report will contain three
sections: screenshots, group responses, and
individual reflections.
Figure 4. Amazon Blueprints
4. LAB REPORT
Screenshots
Add (at least) these screenshots to your group’s
lab report. Provide a caption or brief description
of each.
1. Showing the IP and MAC addresses of
your smart plug
2. From the smart plug app, showing your
plug is connected your wireless network
3. From the Alexa app, showing your plug is
connected to your Echo.
4. From the Alexa app, showing the steps in
your routine
5. From IfThisThenThat, showing the steps
to configure your applet

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 74
https://isedj.org/; https://iscap.info
Group Responses
With your group, discuss and write responses to
these questions:
1. What is the approximate cost of a smart
plug such as the one you are using?
Provide a link to where you can purchase
one.
2. What are the MAC and IP addresses of the
smart plug?
3. Why do you have to set up the plug
before connecting it to the Echo?
4. To which wireless network are you
connected?
5. Why do you need to be on 2.4Ghz rather
than 5 GHz?
6. How are advances in 5G technology
impacting the use of IoT?
7. Describe the role of APIs (application
programming interfaces) in sharing data,
and the services whose APIs you used in
this activity. Why would companies
provide access to their data through
APIs?
Individual Reflections
Each student should answer these questions
individually.
1. Have you previously used a smart
speaker or connected smart devices to it?
2. How might you use a smart speaker and
smart devices in your room or home?
3. What other devices have you seen or
used that are connected to the Internet?
4. What concerns do you have about the use
of IoT related to privacy and security of
your data?
5. What did you learn by completing this
activity? Did anything surprise you?
6. Did you run into any technical problems
while completing this activity? What
happened, and what steps did you take to
you troubleshoot the problems? Were you
able to resolve these issues?
7. How might we improve this activity?
Discuss your responses with your group.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 75
https://isedj.org/; https://iscap.info
Appendix 1. Additional Figures
Figure 5. Steps to add a Smart Plug to a Wireless Network
Figure 6. Steps to Configure a Smart Plug using a Mobile App.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 76
https://isedj.org/; https://iscap.info
Figure 7. Turning on and off the light using the Smart Plug app.
Figure 8. Steps to Connect Amazon Echo to a Wireless Network

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 77
https://isedj.org/; https://iscap.info
Figure 9. Steps to Create an If This Then That Applet

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 78
https://isedj.org/; https://iscap.info
Appendix 2. Creating a Skill with Amazon Blueprints
This Appendix describes steps for creating a skill with Amazon Blueprints. You can run Amazon Echo
skills using any Echo-enabled device or the Alexa app on your mobile device.
Visit http:://blueprints.amazon.com. Select the blueprint you wish to customize. In this example, select
Flashcards in the Learning & Knowledge section. Next, click Make Your Own. See Figure 10.
Figure 10. Create the Flashcards Skill
Add the topic and information for the flash cards. See Figure 11.
Figure 11. Add Topic and Information
Click Experience.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 79
https://isedj.org/; https://iscap.info
Enter information to customize the greetings, sounds, and feedback for users of this skill. See Figure
12.
Figure 12. Add Customizations
Name your flashcard set. See Figure 13.
Figure 13. Name Your Flashcard Set
Click Create Skill to create the skill. This may take a few moments. See Figure 14.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 80
https://isedj.org/; https://iscap.info
Figure 14. Create Your Skill
Say “Alexa, open internet flashcards” or “Alexa, start internet flashcards.” to test your skill using your
Echo device or the Alexa app on your smartphone or mobile device.
You can edit the skill at any time using Amazon Blueprints.
You can decide who has access to your skill, as shown in Figure 15.
• Keep your skill private so only the devices on your home network can access it
• Click Share with others to get a link to share by email or on social media sites so your friends
and followers can access your skill
• Click Publish to Skills Store to publish your skill to the Alexa Skills Store for anyone to find, use,
and review.
Figure 15. Share and Publish Your Skill

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 81
https://isedj.org/; https://iscap.info
Appendix 3. Resources
This appendix contains information about resources described in this lab activity.
Websites
• Amazon Alexa (web interface to Alexa app with limited functionality): http://alexa.amazon.com
• Amazon Blueprints (for creating skills): https://blueprints.amazon.com
• Flip (collaborative video recording and sharing): http://flip.com
• If This Then That (automate apps and devices): http://ifttt.com
Apps
Install these apps on your mobile device. They are available from Google Play or Apple’s App Store.
• Alexa
• Flip (collaborative video recording and sharing)
• If This Then That (automate apps and devices)
• SmartLife (for controlling GoSund brand smart plugs)

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 82
https://isedj.org/; https://iscap.info
Teaching Case
A Registration System for a Citywide Service
Project: Design & Development Case
Dana Schwieger
Department of Management
Southeast Missouri State University
Cape Girardeau, MO 63701, USA
Hook
Baker Street Church is faced with an unexpected yet wonderful problem. Recent publicity has turned
their small service activity into a community-wide event rendering their volunteer management system
obsolete. They are seeking help in developing a database that can handle their growing list of projects
and volunteers.
Abstract
Many small organizations sponsor events and activities that could benefit from the data management
and reporting capabilities provided through a centralized database. However, many of those
organizations do not have the budget to afford a commercial solution or an on-going subscription to a
cloud-based solution for a small scope event with limited frequency use. The case focuses upon a service
project volunteer management system for recording, managing, and reporting on volunteers and the
service projects they are doing. The case provides a realistic scenario that can be used in a systems
analysis and design, database development, or graduate level management information systems course.
Multiple assignment options are provided allowing instructors to select an assignment based upon course
material coverage. Suggested assignments include the development of process modeling diagrams such
as a data flow or swim lane diagrams and database design and development artifacts.
Keywords: Teaching case, Database design, Process design, Swimlane diagrams
1. CASE SUMMARY
Baker Street Church in Whispering Hills, Missouri,
is hosting their second annual “Day of Blessings”
event for the community. The outpouring of
interest has been more than they had anticipated.
They are facing the impossible task of matching a
mountain of volunteers to an equally
overwhelming pile of service projects. The event
has outgrown the capabilities of their spreadsheet
and sticky-note matching process that was used
the previous year. They seek the assistance of a
local MBA student to help them develop a
database solution to fill the gap.
2. CASE TEXT: A GOOD PROBLEM TO HAVE
Mike Green, pastor of Baker Street Church in
Whispering Hills, MO, stared at the unending list
of new email in his Outlook In box. The deadline
for submitting service project ideas for their “Day
of Blessings” initiative was hours away and the
thought of matching the community projects and
needs with volunteers was daunting.
The Day of Blessings initiative was relatively new.
The event got off to a slow start the previous
year, so he was not expecting much of a turnout
this year either. However, a local personal
interest story, with roots in last year’s initiative,

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 83
https://isedj.org/; https://iscap.info
was making current news headlines and the
outpouring of interest was overwhelming. The
church phone lines had been ringing nonstop with
people suggesting projects to do and volunteers
wanting to help with this year’s event.
His thoughts were interrupted by a knock at the
door. Jenny, the church administrative assistant,
had a stack of papers and messages. “Mike,” she
said, “you kind of have that ‘deer-in-the-
headlights’ look about you. I think what I’m about
to give you is just going to add to it.”
“More projects?” Mike asked as he motioned for
Jenny to come in and be seated.
“Yes, more projects AND volunteers,” Jenny said
emphasizing the ‘and’ in her reply. “It’s a good
problem to have.”
“I totally agree with you on that,” Mike said, “but
matching all of the people to the projects without
accidentally leaving something or somebody out
is going to take more time than we have
available. I don’t know how we’re going to be able
to get it done. Last year, we had a small stack of
projects and volunteers. We were able to use
spreadsheets and different color sticky notes to
get projects and people matched. I don’t think it
will be that simple this year. With that many
people involved, we’re going to have to do a lot
more communicating, generating reports, and
handling logistical issues. It would be nice if we
had some sort of registration and reporting
system to help us with this project. I’m sure there
are some out there, but we don’t have time to go
through the budget approval process to get the
money approved to research, purchase, learn,
and setup a new system before the big event.”
Jenny thought for a moment and offered, “There’s
a new MBA student in our class for college-aged
students who stopped by the church office the
other day. He asked if there were any computer-
type requests in the list of Day of Blessings
projects that he could volunteer to do. I took
down his name and number and told him I would
get back to him. I’ll give him a call to see if he
can help us with this. I can check your schedule
and arrange a meeting if it sounds like something
he can do.”
3. THE MEETING
Jenny was able to arrange a meeting with David,
the new MBA student, for early the next day.
David arrived at Mike’s office ready to take notes.
“Pastor Mike,” David said as he stuck out his hand
in greeting, “it’s good to see you today. This
project came just at the right time! I’m supposed
to design and build a database for my
management information systems course at
school. The deadline to submit a project idea is
almost here. What Jenny told me about the
system you are needing sounds like it will work
for my project. Could you go over the steps of the
process and the data needs with me so that I can
take notes to figure out what you need and to put
something together to turn in for my class?”
“Of course, David,” Mike said as he motioned
towards a chair in his office. “I hope this works
out for both of us. Just to give you a little
background, last year was the first time that we
ever hosted the Day of Blessings event. With all
of the hard things going on in our community, we
thought it would be good to do something nice for
everyone and to try to bring the community
together a bit. Although the event involves people
of all ages performing community service projects
over an eight-hour period of time on a Saturday,
there’s a lot of work that takes place behind the
scenes in planning, coordinating, and carrying out
the event.”
Service Project Examples
“In preparation for the upcoming service day,”
Mike said, “we ask the church congregation if they
are aware of, or have any ideas for, service
projects that we can do as a church. We also
contact various local organizations and agencies
to see if there are any projects that they might
have for us to do too.
“Organizations are welcome to submit more than
one project. Some examples of projects that we
did last year include purchasing and installing
playground equipment at a local private school,
painting a mural in the play area of a local public
school, helping an older couple in church paint
their house, building a ramp for a person who
would soon be coming home from the hospital,
making and delivering food baskets in a lower
income area of town, taking lunch to our local fire
department, and buying gift cards for our local
police station.
“The projects range from needing just a couple of
people with any skill level to multiple people with
specific skills. We also have a certain amount of
money allocated in our church budget to pay for
the supplies needed for the event activities, so we
try to stay within our budget.”
Service Project Data
“As you would guess,” Mike continued, “in order
to carry out all of those service projects, there’s
a lot of data that we have to collect about the

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 84
https://isedj.org/; https://iscap.info
activity besides the service project name and
description. We also need to have a contact name
with contact information such as the organization,
email, phone, and address; the address at which
the activity will take place; the amount of time
the project will require; the number of people
needed to perform the project; the skills needed
to perform the project; the supplies and quantity
needing to be purchased for each project; project
supplies provided that will not need to be
purchased; the actual cost and number of
supplies purchased for each project; the date the
supplies were purchased; and the estimated
amount of time needed for the project with the
requested people.”
“Bob, the Facilities Director, and I will use the
supply list report to purchase all of the supplies
before the big day. We will need to record the
date when purchases are made, the quantity of
each item purchased for each project, and the
amount paid. We should also include the name of
the vendor from whom the supplies were
purchased so that we will have this information to
reference if something needs to be returned and
for future supplies. Once the purchases are made,
I will give the receipts to Jenny, and she will be
able to enter the purchase details into the system
and store the receipts in the folder she keeps for
this event.”
Volunteer Data
“In order to carry out all of those projects,” Mike
said, “we need to have volunteers. Last year, we
created a catalog of projects including the project
name, description, location, contact, estimated
time commitment, as well as the number of
people needed. The catalog was posted to the
church’s website along with a downloadable form
that volunteers could fill out and give to the
church office with the name of the project they
were interested in, special skills they offered,
their name and address information, gender, age
category, volunteer type (church or community
member) as well as their willingness to take the
lead on a project. Due to the short timeframe in
which our projects were completed, volunteers
could only sign up for one project. That restriction
applies for this year too.
“We didn’t have a lot of projects or volunteers last
year, so we just created a spreadsheet for each
project and volunteer list and kept them at the
lobby welcome desk.
“We didn’t know what to expect this year. We
anticipated a little growth, but nothing like what
we are experiencing. Thanks to the local media,
this year is a different kind of animal. Last year,
one of our service projects involved repairing the
roof of an unemployed single mother and helping
her get some bedroom furniture for her kids. After
getting to meet her and learn of her plight, one of
the volunteers hired her to work at his business.
She has just blossomed in her role with the
company. During a ‘person on the street’
interview about the current state of the economy
by the local news media, she told them her story
and now it seems like the entire community wants
to get involved helping others. Thus, our need for
a database.”
“I see,” David paused and then jotted down more
notes. “What kind of reports do you think you’ll
need throughout the process?”
Reports
“Well,” Mike replied, “the first type of report we
will need is the catalog of service projects so that
we can make everyone aware of the projects
available and their details. Speaking of projects,
we would also need to have a ‘shopping list’
providing a compilation of all of the supplies that
need to be purchased for each of the projects
before the day of the event. This would need to
be printed in order of supplies needed as well as
include the name of the project for which it will
be used. On the day before the event, we could
use that same report as a check-off sheet to make
sure that each project had the supplies.
“We would also need a volunteer list for each of
the projects so that we would have the names,
phone numbers, and age category of the
volunteers. We would also want to include the
project leader on that sheet. The report would
have to be printed in order of project. Also, on the
day of the event, we could use that report as a
check-in sheet so that we can make sure that
each project has enough people and to get them
into the right groups.
“A project summary sheet containing the project
names, a description of each project, the location
of the activity, the contact for that activity, and
the contact’s phone number would also be
beneficial. The event coordinators would need
these sheets so that they could get in contact with
specific groups and individuals. I can give you
copies of the reports that we had last year”
(Appendix A).
Communication
“With the event being so new and small last
year,” Mike continued, “communicating lists and
event details was fairly easy. However, there are
going to be a lot more people involved in the
event this year, both in and outside the church.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 85
https://isedj.org/; https://iscap.info
I’m going to have to send more specific emails
targeted towards each project. It would be great
if the database could send an email ‘report’ to
project leaders with the information about their
event and the contact information for the people
signed up for their activity. I could send that
email out two or three times before the event.
You may be able to think of some other emails or
reports that would be helpful, but those are the
ones that come to mind.”
Equipment Needed
David thought for a moment and then asked,
“Since obtaining the funds to purchase a new
database system is going to be a problem, will
you have the resources to actually run the
database before and during the event?”
Mike took a sip of his coffee before answering.
“I’ve already been thinking about that. The
children’s program has grown significantly over
the past few years. We anticipated upgrading the
computers in the children’s check-in process this
year and $6000 was allocated in the budget to
purchase three new laptops, two tablets, a
printer, and any additional hardware required. I
think we could go ahead and purchase the new
equipment and use it for the Day of Blessings.
Once we are done with the equipment, it can be
installed in the children’s check-in area. Since
both processes focus upon checking people in, the
memory, storage, and speed requirements should
be similar.
“With so many people expected to be involved in
the Day of Blessings event this year,” Mike
continued, “we are going to have to have multiple
event day check-in areas set-up. We’ll probably
have to set up three standalone tables each with
a laptop in the north parking lot. Two of the tables
will handle event day walkup registrations. The
third table will be the ‘command center’ table to
handle registration problems and printing extra
reports, so this table will also need a printer. To
move people with advanced registrations through
the event day check-in process more quickly, we
will have two lanes on the parking lot where
people can check in while sitting in their cars. A
volunteer with a tablet will go from car to car
checking people in. Since we will be in the parking
lot, we will also need some sort of mobile internet
access. Do you have any hardware
recommendations that you could make for us?”
Wrapping Up
“Not off of the top of my head,” David said as he
continued writing notes, “but, I’ll see what I can
find to recommend. I’ll also see if I can find a
commercial volunteer management system,
similar to what you are wanting, so that you can
see what data they collect and reports they run.
I know you are unable to buy it at this time, but
it may give us some ideas. I would like to create
data flow and process models of what I think you
are seeing your data collection and reporting
processes looking like so I can make sure we are
on the same wavelength. I’ll try to send you
something by the end of the week.”
4. ASSIGNMENTS
This project could take multiple paths depending
on the role your instructor has for you. Clarify
with your instructor the role that you will play.
Request for Proposal (RFP)
Assume the role of David, the MBA student and
conduct an Internet search to find a commercial
volunteer management system that will fit the
church’s need for the Day of Blessings event. Mike
is ready to acquire and implement the commercial
system. His first step is to solicit vendor bids to
obtain the technical infrastructure to support the
new system.
1. From the church’s perspective, develop
the functional and technical requirements
that would be included in a request for
proposal (RFP).
2. From a potential vendor’s perspective,
develop the vendor’s response to the RFP
for the technical requirements.
Essentially, you are proposing the
hardware, software, networking,
installation, documentation, and training
that will be required to implement the
infrastructure.
3. As the documents are developed, record
any assumptions you make, regarding
the processes, in a separate document.
Process Model Diagrams
Assume the role of David, the MBA student and
draw out the functional process steps to verify
that you have identified all of the steps and
understand how the process works.
1. Create diagrams modeling each of the
processes.
2. Write short narratives to accompany your
diagrams to verify and support your
interpretation of the processes.
3. As the diagrams are developed, record
any assumptions you make, regarding
the processes, in a separate document.

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 86
https://isedj.org/; https://iscap.info
Data Flow Diagrams
Assume the role of David, the MBA student and
create a data flow diagram to illustrate the flow
of data through the volunteer management
process to verify that you understand how the
data is collected, processed, stored, and
disseminated.
1. Create a diagram modeling the flow of
data through the process.
2. Write a short narrative to accompany
your diagram to verify and support your
interpretation of the process.
3. As the diagrams are developed, record
any assumptions you make, regarding
the processes, in a separate document.
Systems Analysis Design and Database
Development
Assume the role of David, the MBA student. Mike
does not have the budget to purchase a
commercial volunteer management system. He
wants you to build the database. He wants to:
1. Accumulate the functional and technical
requirements for the system.
2. Prioritize the requirements.
3. Create system development diagrams.
4. Create a data dictionary.
5. Create data entry forms.
6. Create queries to generate records
needed for service project clients; service
project descriptions and resources
needed; available volunteers; service
project volunteer lists; resource shopping
lists; and data needed for various mail-
merged letters (e.g., thank you letters).
7. Create reports for the queries including
service project client information lists,
service project opportunity descriptions
and resource needs lists, available service
project volunteer lists; resource shopping
lists; and informational letters to service
project clients and thank you letters to
volunteers.
8. As the database is developed, record any
assumptions that you make in a short
report.
5. CONCLUSION
David worked all week developing and clarifying
the diagrams. He watched Pastor Mike’s face
expectantly as he explained the diagrams and his
vision for the database. A slight grin began to
stretch across Mike’s face as David finished
explaining his last diagram. “David,” Mike
breathed, “That’s great! I think you know exactly
what we are needing. I can’t wait to start using
your new database!”

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 87
https://isedj.org/; https://iscap.info
Appendix A

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 88
https://isedj.org/; https://iscap.info

Information Systems Education Journal (ISEDJ) 21 (2)
ISSN: 1545-679X May 2023
©2023 ISCAP (Information Systems and Computing Academic Professionals) Page 89
https://isedj.org/; https://iscap.info
